
The 4 Main Types Of Spoofing Attacks And How To Prevent Them Some of these hoaxes piggyback on human gullibility, while others cash in on exploiting hardware or software flaws. out of all the nefarious scenarios that fit the mold of a spoofing attack, the following 11 types are growingly impactful for the enterprise these days. We’ll look at the most common types of spoofing attacks that organizations encounter on a daily basis. we’ll also look at how these attacks can be detected before looking at how to prevent them altogether in the next section. here is a list of spoofing attack types: arp spoofing attack; ip spoofing attack; mac spoofing attack; email.

The 4 Main Types Of Spoofing Attacks And How To Prevent Them In this section, we’ll explore 12 common types of spoofing, complete with real life examples to help you recognize and avoid these threats. 1. email spoofing is when cybercriminals send bogus emails to deceive recipients using email addresses that appear nearly identical to trusted organizations or contacts. Some of the different types of spoofing attacks include call spoofing, email spoofing, website spoofing and ip spoofing. continue reading to learn more about spoofing attacks, the seven common types of spoofing attacks and how to stay protected from them. In this article, you will learn about various types of spoofing attacks, including email, caller id, and website spoofing. you’ll find out how these attacks work, the common signs to look out for, and the best strategies to protect yourself (i highly recommend installing antivirus software like norton). Below, we outline the most common types of spoofing attacks, how they work, and how to recognize them. email spoofing: fraudulent emails that look like they come from trusted contacts. caller id spoofing: fake phone calls from legitimate looking numbers. ip spoofing: hiding the real origin of cyberattacks.

Top 10 Types Of Spoofing Attacks And How To Protect Your Data Tech In this article, you will learn about various types of spoofing attacks, including email, caller id, and website spoofing. you’ll find out how these attacks work, the common signs to look out for, and the best strategies to protect yourself (i highly recommend installing antivirus software like norton). Below, we outline the most common types of spoofing attacks, how they work, and how to recognize them. email spoofing: fraudulent emails that look like they come from trusted contacts. caller id spoofing: fake phone calls from legitimate looking numbers. ip spoofing: hiding the real origin of cyberattacks. Learn what spoofing attacks are and the common types that are used by hackers. understand how to detect and prevent yourself from spoofing attacks. read more. Spoofing attacks represent a significant threat in the digital landscape, but you can mitigate these risks by staying informed and taking proactive measures. understanding the tactics used by cybercriminals and implementing robust security protocols are crucial steps in protecting your data and maintaining trust with your clients and stakeholders. Cybercriminals use various types of spoofing attacks. these attacks aim to gain illegal access, extract sensitive information, or deceive people into executing unwanted activities. understanding the many forms of spoofing attacks and implementing effective prevention measures are critical in protecting ourselves and our companies from these.

Top Types Of Spoofing Attacks Gridinsoft Blogs Learn what spoofing attacks are and the common types that are used by hackers. understand how to detect and prevent yourself from spoofing attacks. read more. Spoofing attacks represent a significant threat in the digital landscape, but you can mitigate these risks by staying informed and taking proactive measures. understanding the tactics used by cybercriminals and implementing robust security protocols are crucial steps in protecting your data and maintaining trust with your clients and stakeholders. Cybercriminals use various types of spoofing attacks. these attacks aim to gain illegal access, extract sensitive information, or deceive people into executing unwanted activities. understanding the many forms of spoofing attacks and implementing effective prevention measures are critical in protecting ourselves and our companies from these.
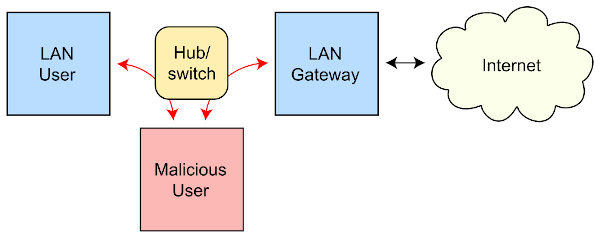
11 Types Of Spoofing Attacks You Should Know About Cybercriminals use various types of spoofing attacks. these attacks aim to gain illegal access, extract sensitive information, or deceive people into executing unwanted activities. understanding the many forms of spoofing attacks and implementing effective prevention measures are critical in protecting ourselves and our companies from these.

7 Types Of Spoofing Attacks And How To Avoid Them
