09b0e6df 5da2 4c74 800d B4aa113e1bec 4096 2304 An antimalware application installed on the remote host is affected by an elevation of privilege vulnerability. the version of microsoft malware protection signature update stub (mpsigstub.exe) installed on the remote windows host is prior to 1.1.16200.1. To choose when and how often you want to scan your pc, use the task scheduler. search for and open schedule tasks. in the left hand menu, open the task scheduler library, then select microsoft >.

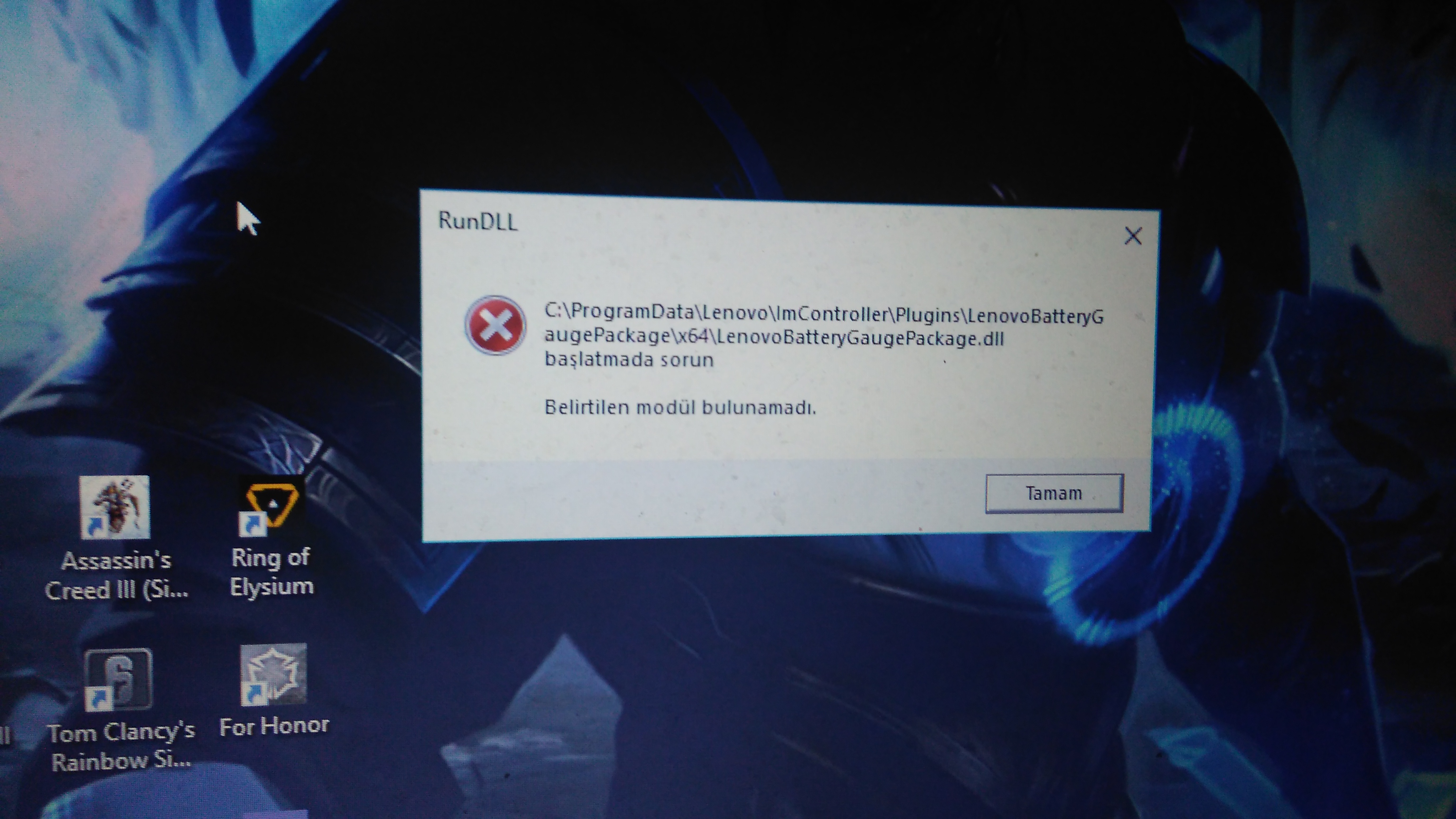
9c2d0d20 73a4 4fc1 8f1d A2b4cc082af4 1921 1080 Seemingly unremoveable infection. posted in virus, trojan, spyware, and malware removal help: ive been fighting to remove this, however it seems like its unremovable. this is a scan from hirens. Trustedsec’s research team has verified that these pocs are valid and have gained code execution on internal test systems. the cve 2020 0688 vulnerability affects the exchange control panel (ecp) component. Microsoft has warned that malicious hackers were able to get the software giant to digitally sign their code so it could be used in attacks, such as the deployment of ransomware. Analysis of the malicious document revealed a “zero day” vulnerability, nicknamed follina, in windows’s msdt url protocol. office applications can virtually execute powershell code by proxy via the ms msdt url scheme. a url scheme is a specification that links urls to specific applications.

5b9f727f 3d19 407b 99a8 0abd3df0b3bb Pdf Microsoft has warned that malicious hackers were able to get the software giant to digitally sign their code so it could be used in attacks, such as the deployment of ransomware. Analysis of the malicious document revealed a “zero day” vulnerability, nicknamed follina, in windows’s msdt url protocol. office applications can virtually execute powershell code by proxy via the ms msdt url scheme. a url scheme is a specification that links urls to specific applications. Cve 2021 40444 is a vulnerability that becomes exploited when attackers create specially crafted, malicious microsoft office documents using activex control. after sending the document, the attacker then tries to convince the victim to open the document so they can gain user rights on a system. Background intelligent transfer service (bits) is used by programmers and system administrators to download files from or upload files to http web servers and smb file shares. bits will take the cost of the transfer into consideration, as well as the network usage so that the user’s foreground work has as little impact as possible. Confidently identify and prioritize exposures from endpoint to cloud with full attack surface visibility and threat aware risk context. rapid7's vulndb is curated repository of vetted computer software exploits and exploitable vulnerabilities.

D0d72591 A3d4 4a53 8c12 9c18772f28e3 Youtube Cve 2021 40444 is a vulnerability that becomes exploited when attackers create specially crafted, malicious microsoft office documents using activex control. after sending the document, the attacker then tries to convince the victim to open the document so they can gain user rights on a system. Background intelligent transfer service (bits) is used by programmers and system administrators to download files from or upload files to http web servers and smb file shares. bits will take the cost of the transfer into consideration, as well as the network usage so that the user’s foreground work has as little impact as possible. Confidently identify and prioritize exposures from endpoint to cloud with full attack surface visibility and threat aware risk context. rapid7's vulndb is curated repository of vetted computer software exploits and exploitable vulnerabilities.
