5 Types Of Network Spoofing To Know

Spoofing Types Guide To Different Types Of Spoofing Here we’ll cover the most common types of network spoofs and how they work. have you ever fallen victim to a network spoofing attack? how is your enterprise prepared against spoofing. Some of these hoaxes piggyback on human gullibility, while others cash in on exploiting hardware or software flaws. out of all the nefarious scenarios that fit the mold of a spoofing attack, the following 11 types are growingly impactful for the enterprise these days.

The 4 Main Types Of Spoofing Attacks And How To Prevent Them Learn about what is spoofing in cyber security, types of spoofing attacks with examples, spoofing vs phishing and the practical prevention measures to help you. From fake emails to forged websites, cybercriminals use a variety of spoofing methods to manipulate trust and steal information. in this section, we’ll explore 12 common types of spoofing, complete with real life examples to help you recognize and avoid these threats. 1. We’ll look at the most common types of spoofing attacks that organizations encounter on a daily basis. we’ll also look at how these attacks can be detected before looking at how to prevent them altogether in the next section. here is a list of spoofing attack types:. Spoofing is a sort of fraud in which someone or something forges the sender's identity and poses as a reputable source, business, colleague, or other trusted contact in order to obtain personal information, acquire money, spread malware, or steal data.
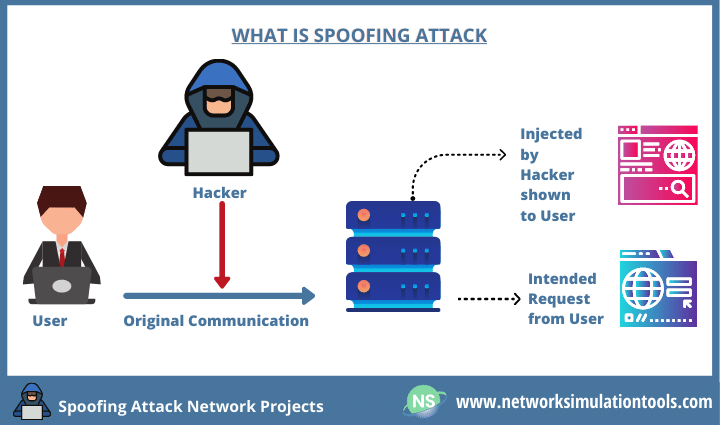
Spoofing Attack Network Projects Network Simulation Tools Network We’ll look at the most common types of spoofing attacks that organizations encounter on a daily basis. we’ll also look at how these attacks can be detected before looking at how to prevent them altogether in the next section. here is a list of spoofing attack types:. Spoofing is a sort of fraud in which someone or something forges the sender's identity and poses as a reputable source, business, colleague, or other trusted contact in order to obtain personal information, acquire money, spread malware, or steal data. Spoofing is when an attacker pretends to be a trusted individual or organization to deceive their target. whether through fake emails, phone numbers, or websites, spoofing aims to trick victims into giving away personal data, passwords, or even making payments to the attacker. Continue reading to learn more about spoofing attacks, the seven common types of spoofing attacks and how to stay protected from them. 1. call spoofing. when you receive a phone call, your phone displays a caller id to reveal who is calling. For attacks to be successful, hackers can spoof many things: an ip address, a web page, a phone number, a login form, a gps location, an email address, a text message, and even a face. some of these actions rely on human error, while others rely on the use of hardware or software flaws. Exploring the realm of cybersecurity, this article delves into a practical spoofing example, demonstrating how attackers use ip address mimicry and social engineering tactics. learn about the techniques, real world scenarios, and preventive measures to safeguard against such threats. lsi keywords: phishing, network defense, mitm attacks.

Top 10 Types Of Spoofing Attacks And How To Protect Your Data Tech Spoofing is when an attacker pretends to be a trusted individual or organization to deceive their target. whether through fake emails, phone numbers, or websites, spoofing aims to trick victims into giving away personal data, passwords, or even making payments to the attacker. Continue reading to learn more about spoofing attacks, the seven common types of spoofing attacks and how to stay protected from them. 1. call spoofing. when you receive a phone call, your phone displays a caller id to reveal who is calling. For attacks to be successful, hackers can spoof many things: an ip address, a web page, a phone number, a login form, a gps location, an email address, a text message, and even a face. some of these actions rely on human error, while others rely on the use of hardware or software flaws. Exploring the realm of cybersecurity, this article delves into a practical spoofing example, demonstrating how attackers use ip address mimicry and social engineering tactics. learn about the techniques, real world scenarios, and preventive measures to safeguard against such threats. lsi keywords: phishing, network defense, mitm attacks.

Spoofing Understanding Types Prevention Methods Fourtrezz For attacks to be successful, hackers can spoof many things: an ip address, a web page, a phone number, a login form, a gps location, an email address, a text message, and even a face. some of these actions rely on human error, while others rely on the use of hardware or software flaws. Exploring the realm of cybersecurity, this article delves into a practical spoofing example, demonstrating how attackers use ip address mimicry and social engineering tactics. learn about the techniques, real world scenarios, and preventive measures to safeguard against such threats. lsi keywords: phishing, network defense, mitm attacks.
Comments are closed.