
Amazon Web Services User Is Not Authorized To Perform Cloudformation Iam policies do not allow restriction of access to specific cloudfront distributions. the work around is to use a wildcard for the resource, instead of only referencing a specific cloudfront resource. The following information can help you identify, diagnose, and resolve access denied errors with aws identity and access management. access denied errors appear when aws explicitly or implicitly denies an authorization request.

Azure Permission Not Authorized To Perform This Operation Stack If you receive an error that you're not authorized to perform the iam:passrole action, your policies must be updated to allow you to pass a role to cloudfront. some aws services allow you to pass an existing role to that service instead of creating a new service role or service linked role. An access denied error message can appear if you’re using incorrect or expired aws sct credentials (access key and secret key) or your iam role or user is missing a required permission to perform an action on a cloudfront resource. There are a couple things you can try to resolve the accessdenied error for kms decryption when accessing an s3 bucket via cloudfront signed url: 1) update the key policy for the kms key used to encrypt the s3 bucket to allow the cloudfront service principal arn:aws:iam::cloudfront:user cloudfront origin access identity to call kms:decrypt on. The error message you're encountering, "user is not authorized to perform: cloudfront:createinvalidation", indicates that the iam user or role you're using doesn't have the necessary permissions to create invalidations for the cloudfront distribution.
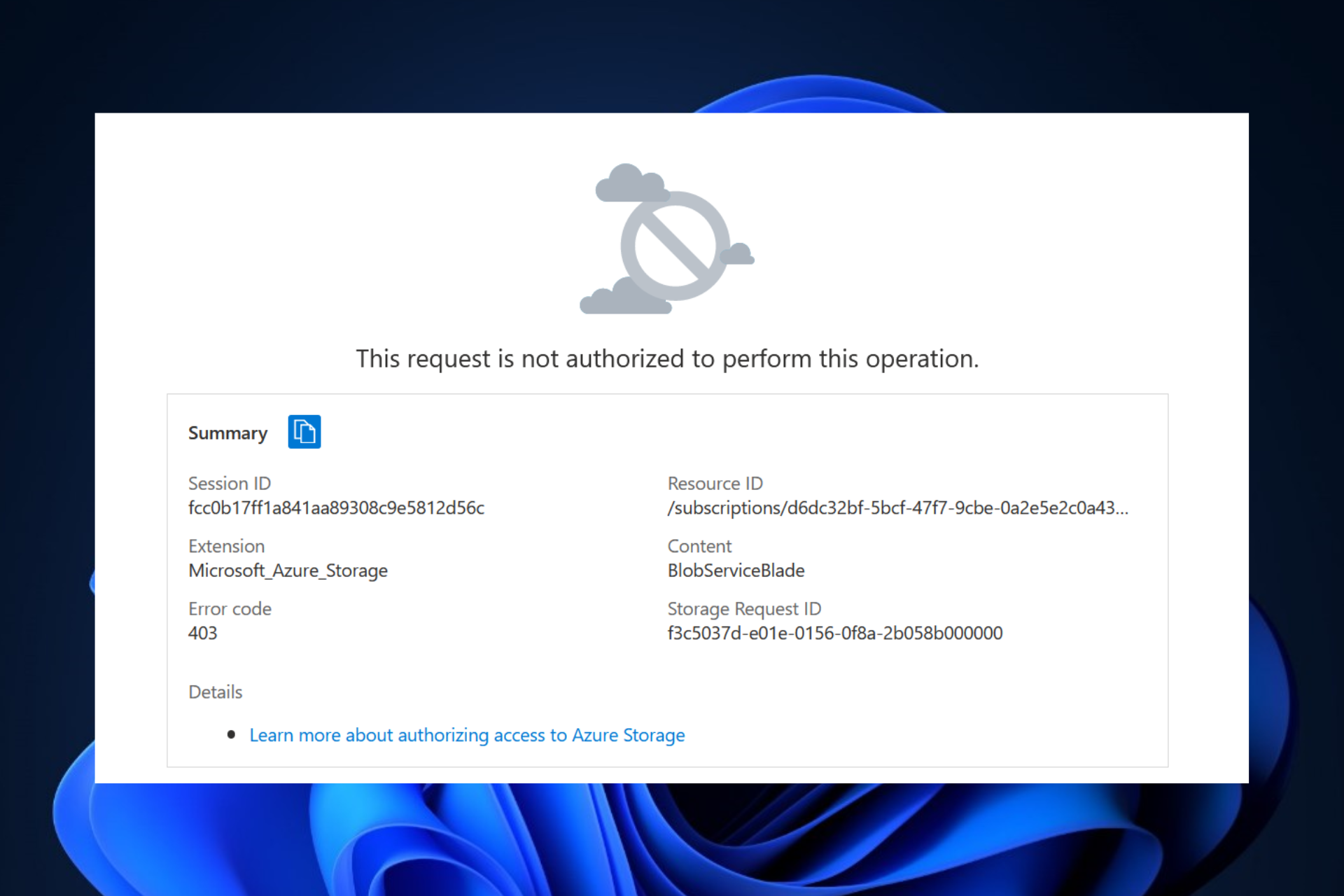
Fix This Request Is Not Authorized To Perform This Operation There are a couple things you can try to resolve the accessdenied error for kms decryption when accessing an s3 bucket via cloudfront signed url: 1) update the key policy for the kms key used to encrypt the s3 bucket to allow the cloudfront service principal arn:aws:iam::cloudfront:user cloudfront origin access identity to call kms:decrypt on. The error message you're encountering, "user is not authorized to perform: cloudfront:createinvalidation", indicates that the iam user or role you're using doesn't have the necessary permissions to create invalidations for the cloudfront distribution. 「スイッチ先のロール名 cm hirai.yuji は、リソース * に対して、 ecr:getauthorizationtoken 権限を有した アイデンティティベースポリシー がアタッチされていない」 というエラーになります。 そのため、下記のポリシーをアタッチすることで、解決します。 次のエラーは、awsマネジメントコンソールにログインしたユーザーがデータベースを作成しようとしたときのエラーになります。 こちらのエラーを分解してみます。 上記をまとめますと、以下のように解説できます. というエラーになります。 そのため、下記のポリシーをアタッチすることで、解決します。 エラー内容がエンコードされている場合、デコードする必要があります。. An error occurred (accessdenied) when calling the assumerole operation: user: arn:aws:iam::123456789:user iam user is not authorized to perform: sts:assumerole on resource: arn:aws:iam::123456789:user iam user. not sure what i am doing wrong. remove the role arn and source profile lines from your config. Learn how to debug cloudfront access denied errors systematically. disable signed urls, check oac oai policies, and verify bucket settings like requester pays to fix access issues. So when you are trying to assume the second role, aws sees it as you trying to assume a role into the second account from the initial account you logged into and not from the account you currently assumed the first role into. if you look in cloudtrail in the initial account, you'll see the assume role entry for the second account in there.
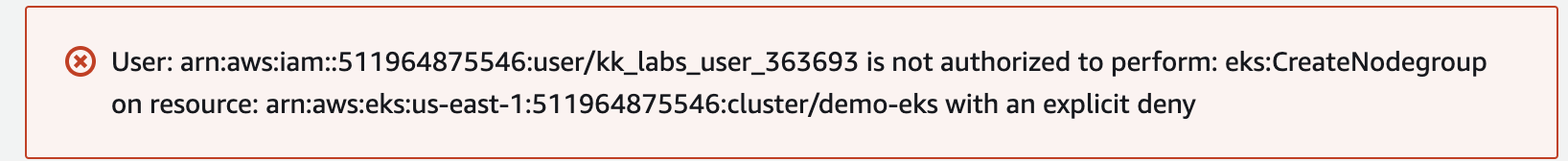
Is Not Authorized To Perform Iam Passrole On Resource Arn Aws Iam 「スイッチ先のロール名 cm hirai.yuji は、リソース * に対して、 ecr:getauthorizationtoken 権限を有した アイデンティティベースポリシー がアタッチされていない」 というエラーになります。 そのため、下記のポリシーをアタッチすることで、解決します。 次のエラーは、awsマネジメントコンソールにログインしたユーザーがデータベースを作成しようとしたときのエラーになります。 こちらのエラーを分解してみます。 上記をまとめますと、以下のように解説できます. というエラーになります。 そのため、下記のポリシーをアタッチすることで、解決します。 エラー内容がエンコードされている場合、デコードする必要があります。. An error occurred (accessdenied) when calling the assumerole operation: user: arn:aws:iam::123456789:user iam user is not authorized to perform: sts:assumerole on resource: arn:aws:iam::123456789:user iam user. not sure what i am doing wrong. remove the role arn and source profile lines from your config. Learn how to debug cloudfront access denied errors systematically. disable signed urls, check oac oai policies, and verify bucket settings like requester pays to fix access issues. So when you are trying to assume the second role, aws sees it as you trying to assume a role into the second account from the initial account you logged into and not from the account you currently assumed the first role into. if you look in cloudtrail in the initial account, you'll see the assume role entry for the second account in there.
User Not Authorized To Use Presenter Cloud Learn how to debug cloudfront access denied errors systematically. disable signed urls, check oac oai policies, and verify bucket settings like requester pays to fix access issues. So when you are trying to assume the second role, aws sees it as you trying to assume a role into the second account from the initial account you logged into and not from the account you currently assumed the first role into. if you look in cloudtrail in the initial account, you'll see the assume role entry for the second account in there.

Azure Devops Api The User Is Not Authorized To Access This Resource
