Api Attack Protection Dont Overlook Your 1 Attack Vector

8 Api Attack Types Api Mike It’s no wonder then that gartner predicts “by 2022, api abuses will be the most frequent attack vector resulting in data breaches for enterprise web applications.”. Explore common api security attack vectors with real world examples, owasp insights & why manual testing is key to catching what scanners miss.

Attack Vector Vs Attack Surface Vs Attack Path Ionix Learn to protect your infrastructure from api attacks. our guide covers 8 common api attack vectors and essential security measures. Threatx co founder and chief strategy officer, bret settle, will discuss the varied types of attack methods used against apis and share strategies for protecting this growing attack surface. We are now facing a new type of threat that uses application programming interfaces (apis) as a primary attack vector. these attacks are sophisticated and disruptive and have already spread across multiple industries. Bola occurs when authorization fails to secure particular data objects in an api. a hacker can gain unauthorized access to users’ data by manipulating the object id sent in api requests. an example is how users retrieve their shopping order information by supplying an order id to an e commerce api.
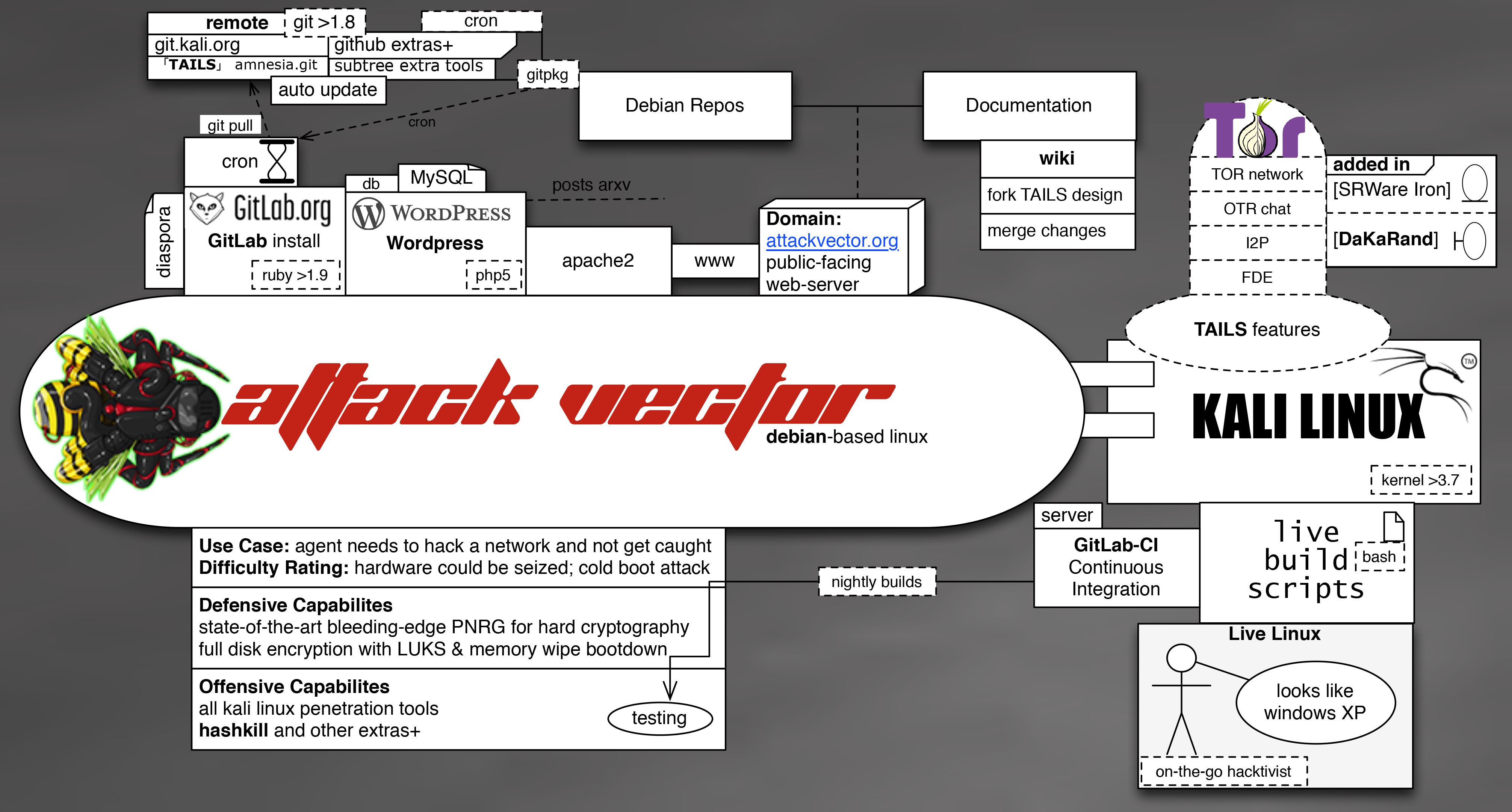
Github Sytabaresa Attackvector Attackvector Linux We are now facing a new type of threat that uses application programming interfaces (apis) as a primary attack vector. these attacks are sophisticated and disruptive and have already spread across multiple industries. Bola occurs when authorization fails to secure particular data objects in an api. a hacker can gain unauthorized access to users’ data by manipulating the object id sent in api requests. an example is how users retrieve their shopping order information by supplying an order id to an e commerce api. This presentation will cover the importance of continuous protection of the complete api risk surface, the need for visibility and assessment of all apis for security risk and compliance status, why alerting teams to malicious traffic is important. Our api threat research repoprt shows shadow apis as the top threat vector. learn more about how to protect your organization. Api attacks are attempts to exploit weaknesses in application programming interfaces – the connectors that let software systems communicate and exchange data. The api heist: how insecure endpoints are becoming the 1 enterprise attack vector "undercode testing": monitor hackers like a pro. get real time updates,.

Github Sytabaresa Attackvector Attackvector Linux This presentation will cover the importance of continuous protection of the complete api risk surface, the need for visibility and assessment of all apis for security risk and compliance status, why alerting teams to malicious traffic is important. Our api threat research repoprt shows shadow apis as the top threat vector. learn more about how to protect your organization. Api attacks are attempts to exploit weaknesses in application programming interfaces – the connectors that let software systems communicate and exchange data. The api heist: how insecure endpoints are becoming the 1 enterprise attack vector "undercode testing": monitor hackers like a pro. get real time updates,.
Comments are closed.