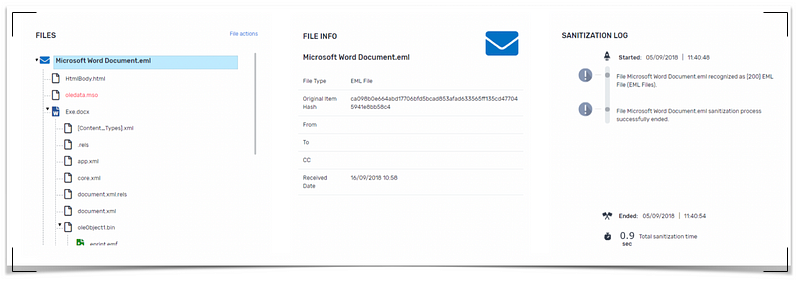
Content Disarm Reconstruction Technology Speaker mr suriya prakashhead – darwis sfs & threat intel apicysecurity corplast three years most of the apt attacks have happened using pdf, doc and image f. Known and unknown threats, including zero day targeted attacks and advanced persistent threats (apt): there are millions of new or modified strains of existing malware released in the wild every year. some are specifically written to target and avoid detection from existing anti virus solutions.

Effective Content Disarm And Reconstruction Filewall for exchange online from odix uses content disarming and reconstruction (cdr) technology to prevent attacks delivered via email attachment, supplementing microsoft 365 exchange online security capabilities. Cdr stands for content disarm and reconstruction. cdr, also known as data sanitization, is an advanced threat prevention technology that does not rely on detection—it follows the zero trust philosophy and assumes all files are malicious, and sanitizes and rebuilds each file ensuring full usability with safe content. Opswat deep content disarm and reconstruction (deep cdr) is an advanced threat prevention technology defeating any file based attacks used for advanced persistent threats (apt’s), ransomware, zero day attacks, etc. Also known as ‘file sanitization’ or ‘content sanitization’ – content disarm and reconstruction (cdr) is an advanced technology providing superior results in the prevention of file based attacks – effectively blocking the initial access phase of most apt’s, ransomware and zero day attacks.
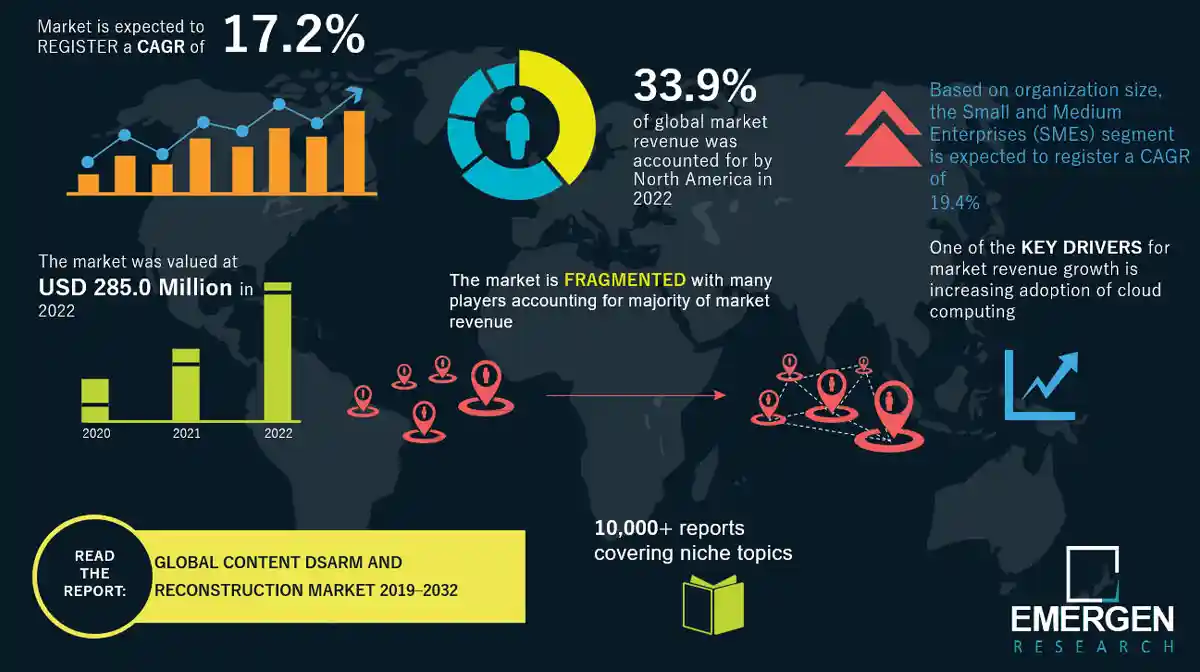
Content Disarm And Reconstruction Market Size Share Industry Forecast Opswat deep content disarm and reconstruction (deep cdr) is an advanced threat prevention technology defeating any file based attacks used for advanced persistent threats (apt’s), ransomware, zero day attacks, etc. Also known as ‘file sanitization’ or ‘content sanitization’ – content disarm and reconstruction (cdr) is an advanced technology providing superior results in the prevention of file based attacks – effectively blocking the initial access phase of most apt’s, ransomware and zero day attacks. An advanced persistent threat (apt) is a sophisticated, long term cyber attack typically conducted by highly skilled threat actors, often backed by nation states or organized cybercriminal groups. unlike typical cyberattacks that seek immediate disruption or financial gain, advanced persistent threats are designed for prolonged, stealthy access to a targeted network or organization. Secureiqlab's content disarm and reconstruction (cdr) validation test underscores the pivotal role of cdr technology in fortifying cybersecurity defenses and safeguarding the integrity of digital assets shared among stakeholders. Can organizations break the “cops and robbers” cycle by thwarting more social engineering attacks and disarming more weaponized documents? this article shares votiro’s novel approach, called content disarm and reconstruction (cdr), which filters out malware by rebuilding the known valid document content. To help organisations from situations mentioned above, cdr (content disarm and reconstruction) also known as threat extraction, proactively protects against known and unknown threats contained in documents image pdf by removing malware, exploits.

Can We Detect Apt Attacks An advanced persistent threat (apt) is a sophisticated, long term cyber attack typically conducted by highly skilled threat actors, often backed by nation states or organized cybercriminal groups. unlike typical cyberattacks that seek immediate disruption or financial gain, advanced persistent threats are designed for prolonged, stealthy access to a targeted network or organization. Secureiqlab's content disarm and reconstruction (cdr) validation test underscores the pivotal role of cdr technology in fortifying cybersecurity defenses and safeguarding the integrity of digital assets shared among stakeholders. Can organizations break the “cops and robbers” cycle by thwarting more social engineering attacks and disarming more weaponized documents? this article shares votiro’s novel approach, called content disarm and reconstruction (cdr), which filters out malware by rebuilding the known valid document content. To help organisations from situations mentioned above, cdr (content disarm and reconstruction) also known as threat extraction, proactively protects against known and unknown threats contained in documents image pdf by removing malware, exploits.
4 Ways To Stop Apt Attacks Using Web Intelligence Recorded Future Can organizations break the “cops and robbers” cycle by thwarting more social engineering attacks and disarming more weaponized documents? this article shares votiro’s novel approach, called content disarm and reconstruction (cdr), which filters out malware by rebuilding the known valid document content. To help organisations from situations mentioned above, cdr (content disarm and reconstruction) also known as threat extraction, proactively protects against known and unknown threats contained in documents image pdf by removing malware, exploits.
