At T Faces Data Breach A Closer Look At Third Party Risk Management Explore the implications of at&t's recent data breach on risk management practices, emphasizing the need for robust third party assessments, advanced security tools, and ai driven solutions to fortify defenses against future threats. In a supply chain attack, hackers target a company's vendors, partners, or other third party providers so as to gain access to its systems or data.

The 2013 Target Data Breach Third Party Risk Management Prevalent At&t's breach highlights the need for continuous assessment and upgrading of security protocols to protect sensitive customer data. it also underlines the criticality of the conversation around third party risk management that all global regulators are now emphasising on heavily. The recent data breach at at&t, impacting nearly all of its cellular customers, underscores the critical need for robust cybersecurity risk management strategies, particularly in the. The data of nearly all customers of the telecommunications giant at&t was downloaded from a third party platform in a security breach, the company said friday, as cyberattacks against businesses, schools and health systems continue to spread globally. Learn about the at&t customer data breach and its security risks, including how stolen data can lead to social engineering, phishing, and ai enhanced attacks. discover steps to protect yourself in the digital age.

The Anatomy Of A Third Party Data Breach Commsec Cyber Security The data of nearly all customers of the telecommunications giant at&t was downloaded from a third party platform in a security breach, the company said friday, as cyberattacks against businesses, schools and health systems continue to spread globally. Learn about the at&t customer data breach and its security risks, including how stolen data can lead to social engineering, phishing, and ai enhanced attacks. discover steps to protect yourself in the digital age. In april 2024, at&t discovered that data was illegally downloaded from a third party cloud service. the stolen data included call and text records for nearly all at&t cellular customers,. Between may 1, 2022, and october 31, 2022, malicious actors exploited a vulnerability within a third party cloud platform utilized by at&t, resulting in the unauthorized download of customer. This case study examines the april 2024 at&t data incident, where customer data was illegally downloaded from a third party cloud platform. the incident, affecting nearly all of at&t's. The data of nearly all customers of the telecommunications giant at&t was downloaded from a third party platform in a security breach, the company said friday, as cyberattacks against businesses, schools and health systems continue to spread globally.
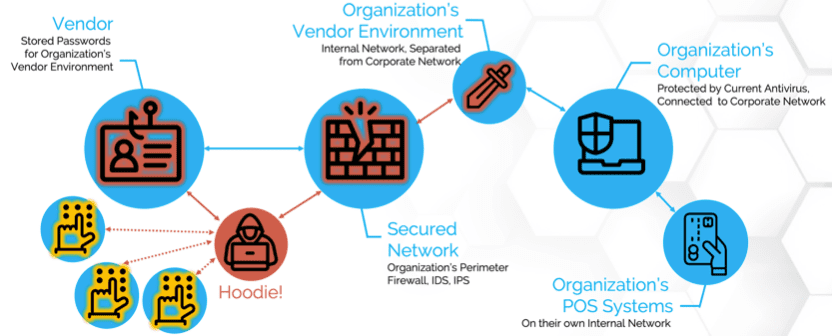
Anatomy Of A Third Party Data Breach Processunity In april 2024, at&t discovered that data was illegally downloaded from a third party cloud service. the stolen data included call and text records for nearly all at&t cellular customers,. Between may 1, 2022, and october 31, 2022, malicious actors exploited a vulnerability within a third party cloud platform utilized by at&t, resulting in the unauthorized download of customer. This case study examines the april 2024 at&t data incident, where customer data was illegally downloaded from a third party cloud platform. the incident, affecting nearly all of at&t's. The data of nearly all customers of the telecommunications giant at&t was downloaded from a third party platform in a security breach, the company said friday, as cyberattacks against businesses, schools and health systems continue to spread globally.

The Escalating Risk Of Core Third Party Data Breaches Breachrx This case study examines the april 2024 at&t data incident, where customer data was illegally downloaded from a third party cloud platform. the incident, affecting nearly all of at&t's. The data of nearly all customers of the telecommunications giant at&t was downloaded from a third party platform in a security breach, the company said friday, as cyberattacks against businesses, schools and health systems continue to spread globally.
