
Spoofing Emails Pdf Email Spam Internet Fraud In this blog, we'll provide a detailed walkthrough on what email authentication protocols are vulnerable to spoofing, how to identify these vulnerabilities at scale, and how to spoof an email address while passing email authentication checks. Learn how to send fake emails using email spoofing techniques in this step by step tutorial. this video is for educational purposes only, helping you underst.

What Is Email Spoofing And How To Protect Yourself Email spoofing is sending emails with a forged senders address. basically, sending an email to anyone, by claiming to be someone else. In this blog we’ll explain email spoofing in more detail, as well as providing a practical guide for how you and your organization can fight this tactic and reduce the risk of successful phishing attempts. what is email spoofing?. What is email spoofing? email spoofing is a common fraud technique used to trick users into believing a email originated from a trusted source when it really originated from a fraudulent source. spoofing is used as a means of phishing; to promote services, collect sensitive data or harvest a bounty. In cybersecurity, email spoofing is a form of sending emails with a fake sender address to make it appear as if the email originates from a trusted source. attackers manipulate email headers to mislead recipients about the real origin of the message.
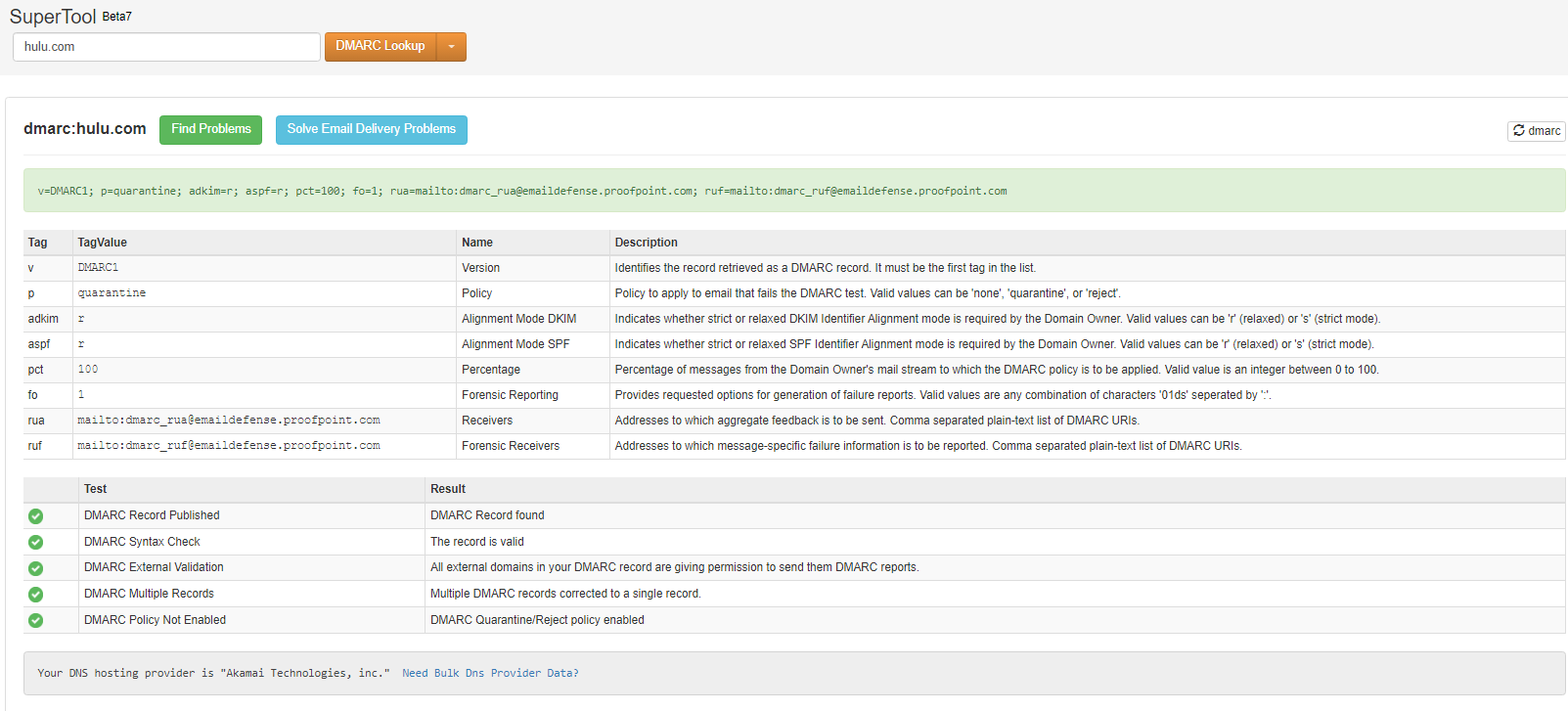
Email Spoofing A Full Guide What is email spoofing? email spoofing is a common fraud technique used to trick users into believing a email originated from a trusted source when it really originated from a fraudulent source. spoofing is used as a means of phishing; to promote services, collect sensitive data or harvest a bounty. In cybersecurity, email spoofing is a form of sending emails with a fake sender address to make it appear as if the email originates from a trusted source. attackers manipulate email headers to mislead recipients about the real origin of the message. Email spoofing is one of the most widely used tactics by cybercriminals, where they forge the sender’s email address to make it appear as if it’s from a trusted source. these emails can range from seemingly urgent messages from your bank to emails from a colleague asking for sensitive information. To understand all of this article, we first need to understand how sending and recieving emails work. Email spoofing involves technically forging the sender address and display name in an email header to disguise the real sender’s identity. the goal is to manipulate the recipient’s trust in that identity to trigger risky actions. In this blog post, i’ll explain what it means to “spoof” an email address, how easy it is for malicious actors to pull off successfully, and the steps you can take today to reduce its impact on your organization. email spoofing refers to the practice of disguising the origin of an email message.
