Hashing Asymmetric Encryption And Digital Signatures The Armchair

Hashing Asymmetric Encryption And Digital Signatures The Armchair Cryptographic algorithms can be categorized into three classes: hash functions, symmetric, and asymmetric algorithms. this article sheds light on their differences, purposes, and main fields of application. For asymmetric encryption, the sender uses a public key to encrypt the data and the receiver uses the private key to decrypt the encrypted data. for signing, the sender uses the private key to create the message's signature and the receiver uses the public key to verify the signature.

Asymmetric Hashing Vs Encryption Explained Using vpn software to encrypt information while it is in transit over the internet in effect creates private communication channels, often referred to as tunnels, which are accessible only to those parties possessing the appropriate encryption and decryption keys. So, this post will explain hashing, hmac's and digital signatures along with the differences between them. hopefully, when asked about these during an interview, you will answer correctly!. Hashing ensures data integrity by creating unique identifiers, encryption protects data confidentiality, and digital signatures provide authentication and authorization for transactions. Now the basics are clear, let’s focus on what a digital signature is and how it makes use of asymmetric cryptography for authentication and verification of software, messages, documents and more.
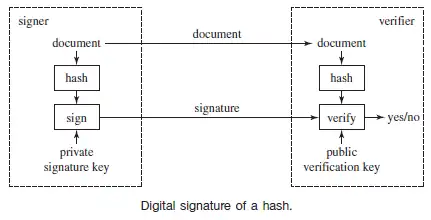
Asymmetric Encryption Network Encyclopedia Hashing ensures data integrity by creating unique identifiers, encryption protects data confidentiality, and digital signatures provide authentication and authorization for transactions. Now the basics are clear, let’s focus on what a digital signature is and how it makes use of asymmetric cryptography for authentication and verification of software, messages, documents and more. Asymmetric hashing vs. encryption explained. understand their security features, applications, and ideal use cases for optimal protection. Even so, there are examples that seem to be one way hash functions: they are easy to compute but we know of no easy way to find a preimage, and examples will follow. Some even combine symmetric and asymmetric encryption, such as hybrid cryptography, and others blend cryptography, hashing, and digital signatures, like signcryption.

Solution Asymmetric Encryption And Hashing Presentation Studypool Asymmetric hashing vs. encryption explained. understand their security features, applications, and ideal use cases for optimal protection. Even so, there are examples that seem to be one way hash functions: they are easy to compute but we know of no easy way to find a preimage, and examples will follow. Some even combine symmetric and asymmetric encryption, such as hybrid cryptography, and others blend cryptography, hashing, and digital signatures, like signcryption.
Comments are closed.