
How To Fix User Is Not Authorized To Perform Sns Tagresource On User: arn:aws:iam::123456789012:user mateojackson is not authorized to perform: sns:getwidget on resource: my example widget. in this case, mateo's policy must be updated to allow him to access the my example widget resource using the sns:getwidget action. if you need help, contact your aws administrator. Learn how to grant permission for users or applications to publish to an amazon sns topic by configuring aws identity and access management (iam) policies. this topic describes methods for adding policies to iam users, groups, or directly to the topic, enabling controlled access and management of publishing permissions across aws accounts.

How To Fix User Is Not Authorized To Perform Sns Tagresource On The error message states the problem quite accurately. the credentials used to create the cloudformation stack (presumably your login credentials unless you specified a role during stack creation) is not authorized to create an amazon sns topic. you should look at the permissions associated with your iam user and add the necessary permissions. 您可以使用以下信息,帮助诊断和修复在使用 amazon sns 和 iam 时可能遇到的常见问题。 如果您收到一个错误,指明您无权执行某个操作,则必须更新策略以允许您执行该操作。 当 mateojackson 用户尝试使用控制台查看有关虚构 my example widget 资源的详细信息,但不拥有虚构 sns: getwidget 权限时,会发生以下示例错误。 在此情况下,mateo 的策略必须更新以允许其使用 sns: getwidget 操作访问 my example widget 资源。 如果您需要帮助,请联系 amazon 管理员。 您的管理员是提供登录凭证的人。. Double check the arn field in the "resource" of you policy. it should be the target topic. i want to publish a message to a topic provided by aws (aws has provided me the topic for integration purposes). on topic the policy has all the actions and my account also has amazonsnsfullaccess. 我在 amazon simple notification service (amazon sns) 中得到一个错误。 错误发生在我使用子网时,期间我尝试从跨账户 amazon elastic compute cloud (amazon ec2) 实例发布我的 sns 主题。 如果在调用 发布 操作时收到授权错误,请完成 验证 ec2 实例 iam 角色和 sns 主题访问策略权限 部分中的步骤。 如果您对使用服务器端加密的 sns 主题存在问题,并且收到 "kmsaccessdenied" 错误,请完成 验证 kms 密钥设置和 ec2 iam 角色权限 部分中的步骤。.
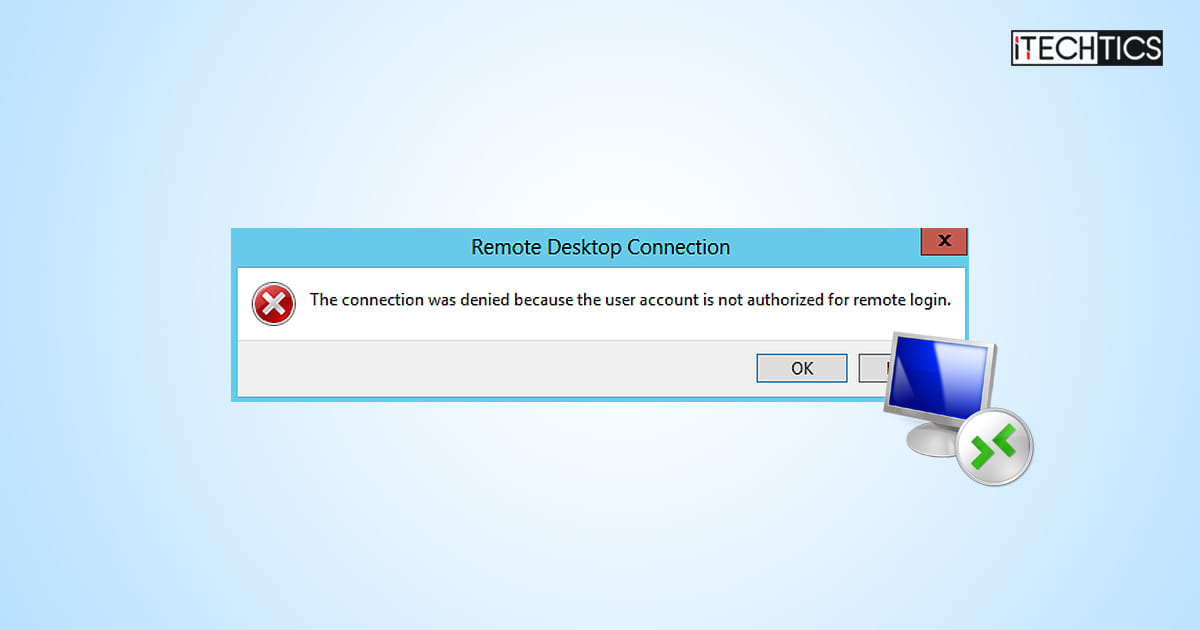
How To Fix User Account Not Authorized For Remote Login Error Double check the arn field in the "resource" of you policy. it should be the target topic. i want to publish a message to a topic provided by aws (aws has provided me the topic for integration purposes). on topic the policy has all the actions and my account also has amazonsnsfullaccess. 我在 amazon simple notification service (amazon sns) 中得到一个错误。 错误发生在我使用子网时,期间我尝试从跨账户 amazon elastic compute cloud (amazon ec2) 实例发布我的 sns 主题。 如果在调用 发布 操作时收到授权错误,请完成 验证 ec2 实例 iam 角色和 sns 主题访问策略权限 部分中的步骤。 如果您对使用服务器端加密的 sns 主题存在问题,并且收到 "kmsaccessdenied" 错误,请完成 验证 kms 密钥设置和 ec2 iam 角色权限 部分中的步骤。. The sns topic needs to have a police where the other account are allowed to publish to it (found on the sns topic settings in aws console. the user role trying to publish needs to have proper policy (the one you published seems fine for that). 我正在尝试创建一个sns主题,并从lambda发布消息。但是我在尝试这样做的时候遇到了授权错误。service: amazonsns; status code: 403; error code: authorizationerror完全例外com.amazonaws.services.sns.model.authorizationerrorexception: user: arn. When an iam entity tries to add a subscription to an amazon sns topic without subscribe api action permissions, sns returns the following error: an error occurred (authorizationerror) when calling the subscribe operation: user: your iam user or role is not authorized to perform: sns:subscribe on resource: your sns topic arn.

Fix This Request Is Not Authorized To Perform This Operation The sns topic needs to have a police where the other account are allowed to publish to it (found on the sns topic settings in aws console. the user role trying to publish needs to have proper policy (the one you published seems fine for that). 我正在尝试创建一个sns主题,并从lambda发布消息。但是我在尝试这样做的时候遇到了授权错误。service: amazonsns; status code: 403; error code: authorizationerror完全例外com.amazonaws.services.sns.model.authorizationerrorexception: user: arn. When an iam entity tries to add a subscription to an amazon sns topic without subscribe api action permissions, sns returns the following error: an error occurred (authorizationerror) when calling the subscribe operation: user: your iam user or role is not authorized to perform: sns:subscribe on resource: your sns topic arn.
