How To Secure Remote Workers And Cloud Access At The Same Time
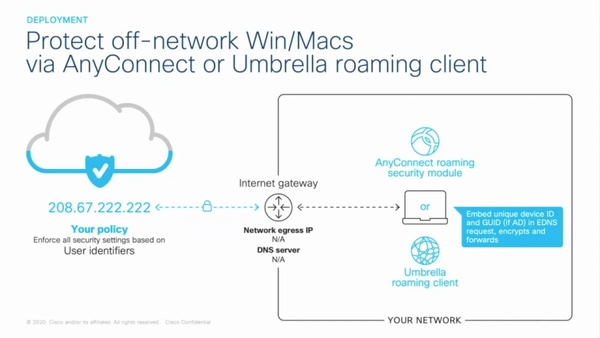
3 Steps To Secure Remote Workers And Students Thought leaders jerald dawkins, ph.d., chris clements, and michael oglesby will introduce ciso edge, a cutting edge cloud first security solution, and how it addresses these challenges head on . For it managers needing to set up cloud services for remote workers, there are several things to consider. these include services for cloud, security, backups, and disaster recovery.

How To Secure Your Remote Workers In this guide, we’ll break down the tools, risks, and best practices that support secure remote work, giving your team the flexibility they need without compromising security. Cps allows an admin to target a user with policies which follow them across all devices, regardless of the way the devices are managed (if at all). we will also share some recommended security settings which might be worth considering. Here, 15 experts from forbes business council look into how a company can implement data security in a remote work environment that won’t disrupt the employees. Remote work is here to stay, and as a result, many organizations are placing a greater emphasis on remote workforce security. if you have employees working from various locations—often using personal devices or unsecured networks—it’s more important than ever to take proactive steps to protect sensitive data and minimize vulnerabilities.

The 10 Best Ways To Secure Remote Access Here, 15 experts from forbes business council look into how a company can implement data security in a remote work environment that won’t disrupt the employees. Remote work is here to stay, and as a result, many organizations are placing a greater emphasis on remote workforce security. if you have employees working from various locations—often using personal devices or unsecured networks—it’s more important than ever to take proactive steps to protect sensitive data and minimize vulnerabilities. Secure remote working refers to the practice of working from a location other than the traditional office environment while ensuring the security of the organization’s digital assets and data. remote work can be done from anywhere, including home, a coffee shop, or a co working space. Best practices include regularly auditing file permissions, enforcing least privilege access, and using cloud access security brokers (casbs) to monitor shadow it. Discover essential strategies for managing cloud access in remote work settings to safeguard your data, and learn how to stay one step ahead of threats. The shift to remote work introduced several security challenges for some organizations. cloud security. employees needed access to cloud services for critical functions, such as customer relationship management, collaboration and file storage. connecting to those services from behind a corporate firewall had provided reasonable protection, but those safeguards weren't available for employees.
Secure Work Remote Secure remote working refers to the practice of working from a location other than the traditional office environment while ensuring the security of the organization’s digital assets and data. remote work can be done from anywhere, including home, a coffee shop, or a co working space. Best practices include regularly auditing file permissions, enforcing least privilege access, and using cloud access security brokers (casbs) to monitor shadow it. Discover essential strategies for managing cloud access in remote work settings to safeguard your data, and learn how to stay one step ahead of threats. The shift to remote work introduced several security challenges for some organizations. cloud security. employees needed access to cloud services for critical functions, such as customer relationship management, collaboration and file storage. connecting to those services from behind a corporate firewall had provided reasonable protection, but those safeguards weren't available for employees.
Comments are closed.