Iot Security Best Practices Strategies For A Secure Iot Ecosystem
Security In The Iot Ecosystem Webinar Series Secure Technology Alliance Discover iot security best practices and strategies to safeguard your iot ecosystem. learn how to secure devices, networks, and data with a robust iot security strategy. Internet of things (iot) devices can be vulnerable to hacking and cyberattacks. learn why this is so and the iot security best practices you can implement to safeguard your devices, networks, and users.
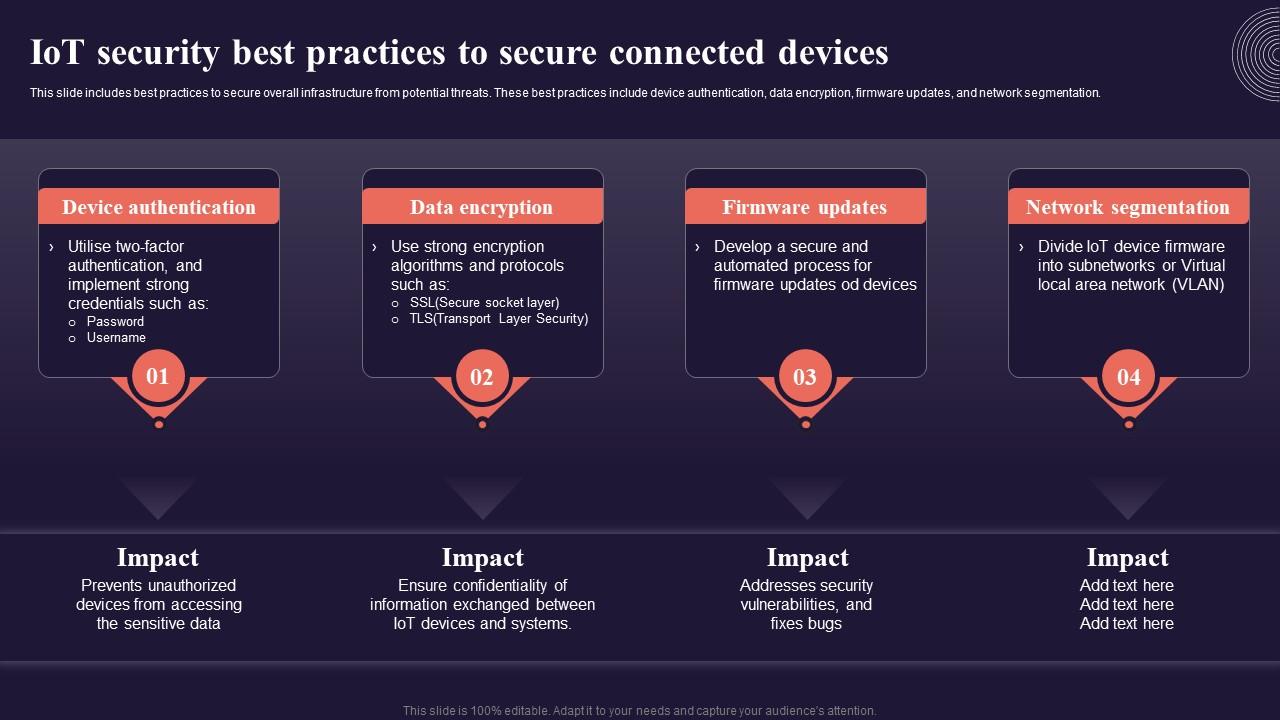
Iot Security Best Practices To Secure Connected Introduction To It is imperative that government and industry work together, quickly, to ensure the iot ecosystem is built on a foundation that is trustworthy and secure. in 2014, the president’s national security telecommunications advisory committee (nstac) highlighted the need for urgent action. There are multiple security practices on the internet of things that are mainly used to protect the internet of things from vulnerabilities. some of the top 10 iot security practices are mentioned below: 1. regularly update the iot devices. Implementing these top 10 strategies can significantly enhance the security of iot deployments. by prioritizing security in connectivity choices, understanding different levels of security, and adopting robust authentication, update, and monitoring practices, businesses can protect their iot ecosystems from a wide range of cyber threats. There are numerous strategies and techniques that businesses can employ to secure iot devices. these include conducting software updates, segmenting networks, encrypting ported data, establishing firewalls, introducing multi factor authentication, keeping up password hygiene, and elevating endpoint security to the top of their cybersecurity stack.

How Secure Is The Iot Ecosystem Implementing these top 10 strategies can significantly enhance the security of iot deployments. by prioritizing security in connectivity choices, understanding different levels of security, and adopting robust authentication, update, and monitoring practices, businesses can protect their iot ecosystems from a wide range of cyber threats. There are numerous strategies and techniques that businesses can employ to secure iot devices. these include conducting software updates, segmenting networks, encrypting ported data, establishing firewalls, introducing multi factor authentication, keeping up password hygiene, and elevating endpoint security to the top of their cybersecurity stack. Securing the internet of things requires a layered defense strategy, ensuring encryption, regular updates, and network segmentation. as iot expands, businesses and consumers must stay vigilant, recognizing risks before they escalate into major security incidents. As the iot ecosystem continues to expand, it's essential to implement effective risk management strategies and best practices to secure it. in this article, we'll explore the key steps to securing your iot ecosystem. To effectively protect iot environments from evolving threats, organizations must adopt a layered security strategy rooted in technical controls, risk driven architecture, and continuous monitoring. Here’s an in depth look at best practices and strategies to secure the iot ecosystem. 1. start with secure boot. think of secure boot as the lock on the front door of your iot.

Atlantic Council Recommendations To Better Secure The Iot Ecosystem Securing the internet of things requires a layered defense strategy, ensuring encryption, regular updates, and network segmentation. as iot expands, businesses and consumers must stay vigilant, recognizing risks before they escalate into major security incidents. As the iot ecosystem continues to expand, it's essential to implement effective risk management strategies and best practices to secure it. in this article, we'll explore the key steps to securing your iot ecosystem. To effectively protect iot environments from evolving threats, organizations must adopt a layered security strategy rooted in technical controls, risk driven architecture, and continuous monitoring. Here’s an in depth look at best practices and strategies to secure the iot ecosystem. 1. start with secure boot. think of secure boot as the lock on the front door of your iot.

Safeguarding Iot Ecosystem To effectively protect iot environments from evolving threats, organizations must adopt a layered security strategy rooted in technical controls, risk driven architecture, and continuous monitoring. Here’s an in depth look at best practices and strategies to secure the iot ecosystem. 1. start with secure boot. think of secure boot as the lock on the front door of your iot.
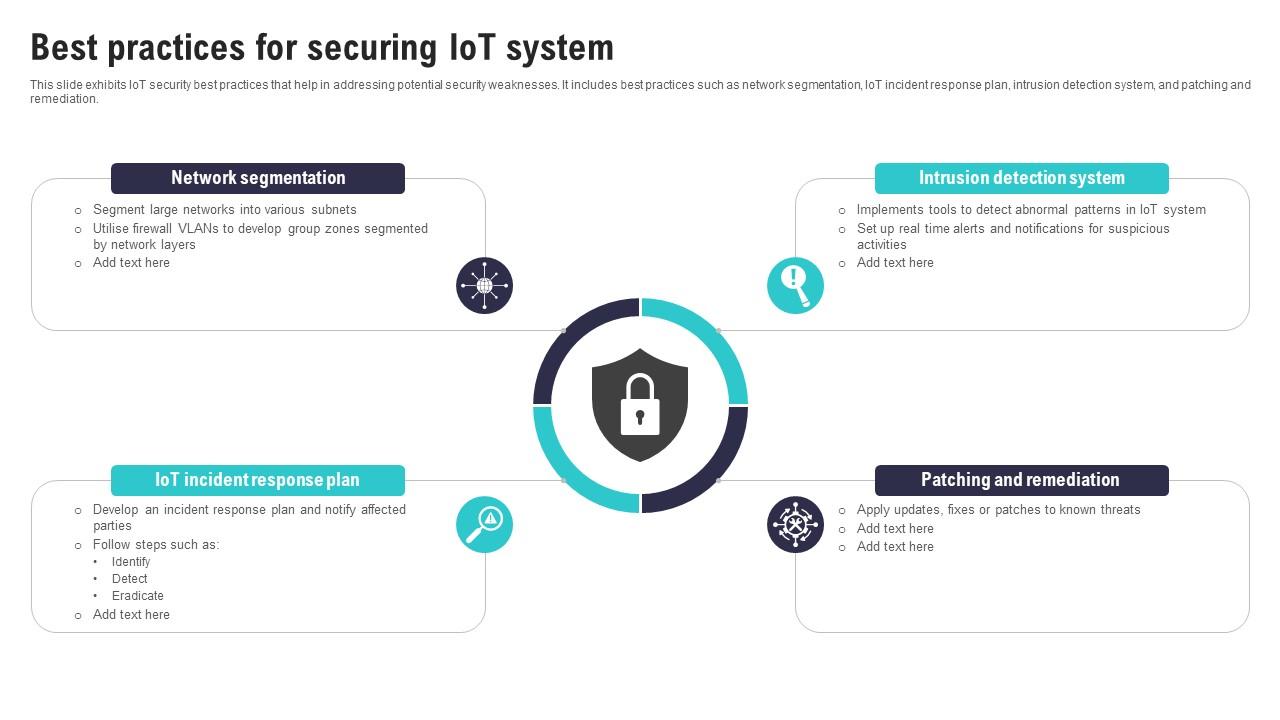
Best Practices For Securing Iot System Iot Security And Privacy
Comments are closed.