
Ip Spoofing Pdf Internet Protocols Transmission Control Protocol Ip spoofing can be used to carry out “man in the middle" (mitm) or “denial of service" (dos) attacks. these methods allow hackers to obtain sensitive data, such as credit card information or social security numbers by interfering with communication between other networked computers. Internet protocol (ip) spoofing is a type of malicious attack where the threat actor hides the true source of ip packets to make it difficult to know where they came from. the attacker creates packets, changing the source ip address to impersonate a different computer system, disguise the sender's identity or both.

Ip Spoofing Attacks What Are They And How Can You Prevent Them Zix There are five things, among others, that you can do to help prevent ip spoofing and its related attacks from affecting your network: use authentication based on key exchange between the. Ip spoofing is a common type of cyber attack. it tricks computer networks into thinking a request comes from a trusted source. hackers can change the ip address to gain unauthorized access to a network. this leads to harmful acts like stealing sensitive data or turning computers into zombies. Ip spoofing can be used for a variety of attacks. once hackers gain your device's trust, they can use that vulnerability to request personal information, send a computer virus, or even turn your device into a zombie to support a large scale bot attack on a target network. can ip spoofing be stopped?. Ip spoofing utilizes false ip address information to hide the identity of the sender of online data. this type of spoofing is particularly common in distributed denial of service (ddos) attacks, as senders use an unknown identity to overwhelm servers that cannot quickly be located and resolved.
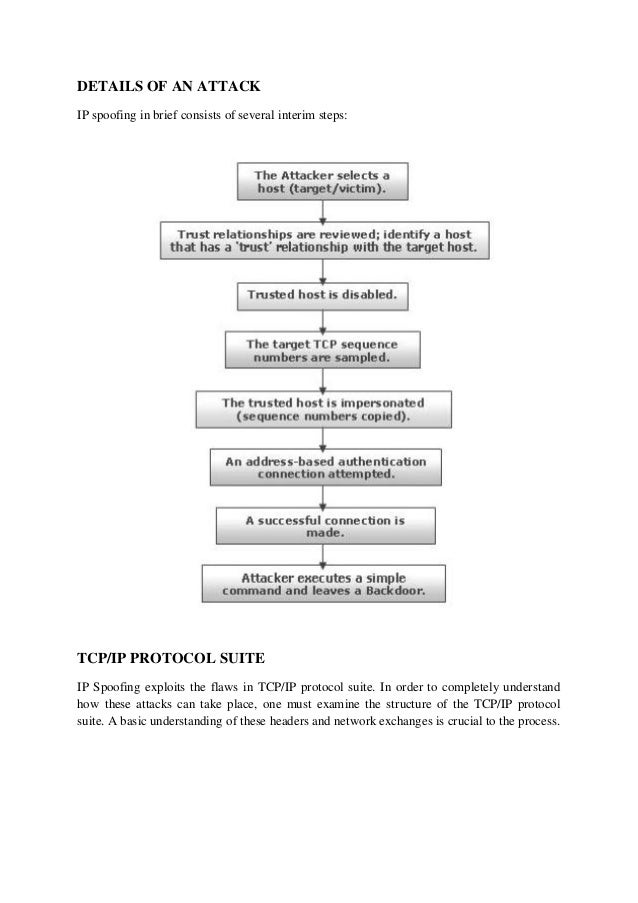
Ip Spoofing Attacks Ip spoofing can be used for a variety of attacks. once hackers gain your device's trust, they can use that vulnerability to request personal information, send a computer virus, or even turn your device into a zombie to support a large scale bot attack on a target network. can ip spoofing be stopped?. Ip spoofing utilizes false ip address information to hide the identity of the sender of online data. this type of spoofing is particularly common in distributed denial of service (ddos) attacks, as senders use an unknown identity to overwhelm servers that cannot quickly be located and resolved. In simple terms, ip spoofing is when an attacker pretends to be someone else online. they do this by changing the source ip address of their packets, making it seem like the data is coming from a trusted source. this can trick networks, servers, and even users into thinking the data is safe. think of it like getting a fake letter in the mail. Ip spoofing, a major threat to internet security, has become a common technique used by cybercriminals to hide their identities and carry out malicious activities. this method allows attackers to manipulate network traffic by spoofing another device’s ip address. Ip spoofing is the process of creating internet protocol (ip) packets with altered source addresses to either disguise the sender’s identity, mimic another computer system, or both. ddos attacks against a target device or the infrastructure around it are frequently launched using this method by hostile actors. Ip spoofing steals the identity of data packets, making it difficult to know the origin of data flows and opening the door to interception attacks. learn how these damaging network security threats work and ways to detect and prevent ip spoofing attacks.
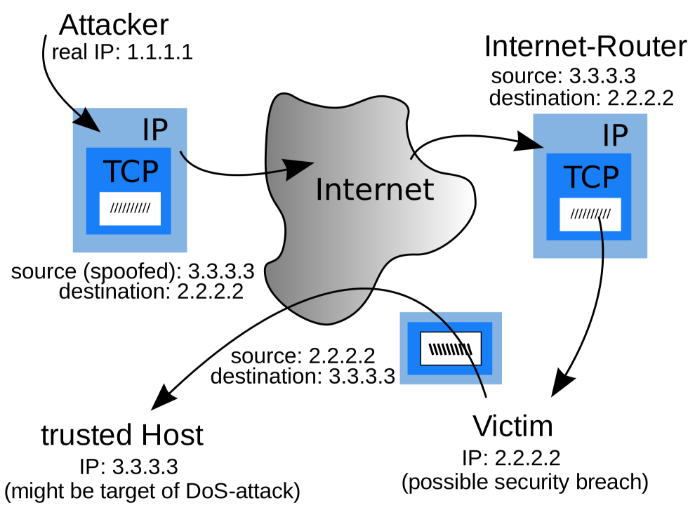
What Is Ip Spoofing And Denial Of Service Dos Attack In simple terms, ip spoofing is when an attacker pretends to be someone else online. they do this by changing the source ip address of their packets, making it seem like the data is coming from a trusted source. this can trick networks, servers, and even users into thinking the data is safe. think of it like getting a fake letter in the mail. Ip spoofing, a major threat to internet security, has become a common technique used by cybercriminals to hide their identities and carry out malicious activities. this method allows attackers to manipulate network traffic by spoofing another device’s ip address. Ip spoofing is the process of creating internet protocol (ip) packets with altered source addresses to either disguise the sender’s identity, mimic another computer system, or both. ddos attacks against a target device or the infrastructure around it are frequently launched using this method by hostile actors. Ip spoofing steals the identity of data packets, making it difficult to know the origin of data flows and opening the door to interception attacks. learn how these damaging network security threats work and ways to detect and prevent ip spoofing attacks.
