
Managing The Advanced Persistent Threat Apt Lifecycle Identity In this paper, we give an overview of advanced persistent threats (apt) attacks life cycle as defined by security experts. we introduce our own compiled life cycle model guided by attackers objectives instead of their actions. Explore the key phases of the advanced persistent threat (apt) lifecycle. learn how apts infiltrate, persist, and exfiltrate data, and strategies to defend against them.
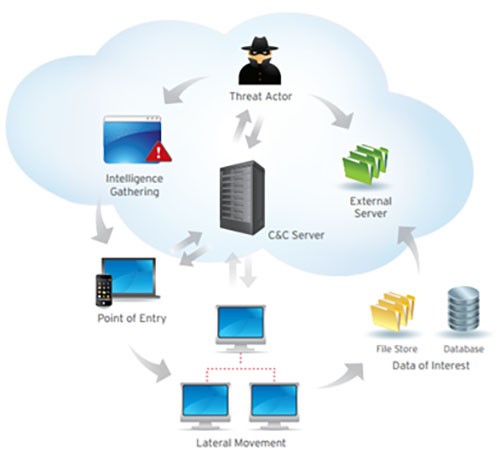
Advanced Persistent Threat Apt Archives Having in house or contract identity and access management (iam) professionals strengthen your company’s policies and protocols for network user access helps to stop apt cyber criminals at nearly every phase of the apt lifecycle. installing firewalls and enabling email protections are standard practices for advanced threat protection (atp). Advanced persistent threats are prolonged cyber attacks designed to infiltrate and data exfiltration. infiltration can be done by intrusion and penetration into the cyber network domain. This presentation will cover the full advanced persistent threat (apt) life cycle and management of the resulting intrusions. it will cover both what the ap. Advanced persistent threat (apt) attacks involve a complex process where attackers use multiple tactics and techniques to infiltrate a target's network, maintain persistence, and steal data:.
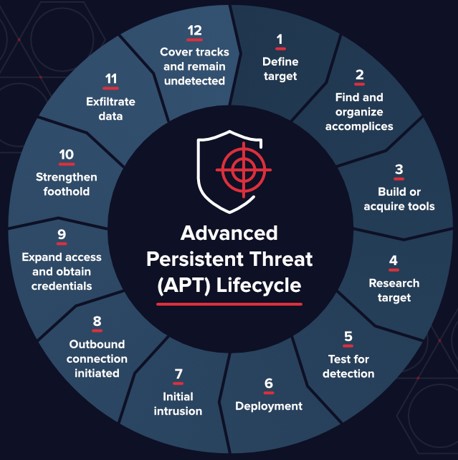
Advanced Persistent Threat Apt Ipspecialist This presentation will cover the full advanced persistent threat (apt) life cycle and management of the resulting intrusions. it will cover both what the ap. Advanced persistent threat (apt) attacks involve a complex process where attackers use multiple tactics and techniques to infiltrate a target's network, maintain persistence, and steal data:. Advanced persistent threats (apt) are emerging trend in cyber security field and many others conducted survey and research on them to understand the adversary attack vectors, strategies and technologies. An advanced persistent threat (apt) is a prolonged and targeted cyberattack in which an unauthorized person (an intruder) gains access to a network and stays there undetected for a long period of time (rouse, 2020; gonzalez, 2014). An advanced persistent threat (apt) is a type of attack campaign in which an unauthorized user gains access to a network and remains there undetected for a prolonged period of time. Apt should be seen as a complex phenomenon, an existing danger to companies, organisations and public entities. this article showcases the problem of apt, the biggest threats related to them, and chosen methods and tools that can be effectively used to counter apt attacks. an effective, multi layered defence model is outlined in the article as.

Pdf Advanced Persistent Threat Apt Training Advanced persistent threats (apt) are emerging trend in cyber security field and many others conducted survey and research on them to understand the adversary attack vectors, strategies and technologies. An advanced persistent threat (apt) is a prolonged and targeted cyberattack in which an unauthorized person (an intruder) gains access to a network and stays there undetected for a long period of time (rouse, 2020; gonzalez, 2014). An advanced persistent threat (apt) is a type of attack campaign in which an unauthorized user gains access to a network and remains there undetected for a prolonged period of time. Apt should be seen as a complex phenomenon, an existing danger to companies, organisations and public entities. this article showcases the problem of apt, the biggest threats related to them, and chosen methods and tools that can be effectively used to counter apt attacks. an effective, multi layered defence model is outlined in the article as.
What Is An Advanced Persistent Threat Apt Characteristics An advanced persistent threat (apt) is a type of attack campaign in which an unauthorized user gains access to a network and remains there undetected for a prolonged period of time. Apt should be seen as a complex phenomenon, an existing danger to companies, organisations and public entities. this article showcases the problem of apt, the biggest threats related to them, and chosen methods and tools that can be effectively used to counter apt attacks. an effective, multi layered defence model is outlined in the article as.
