Personal Data Protection What Are Spoofing Attacks Le Vpn
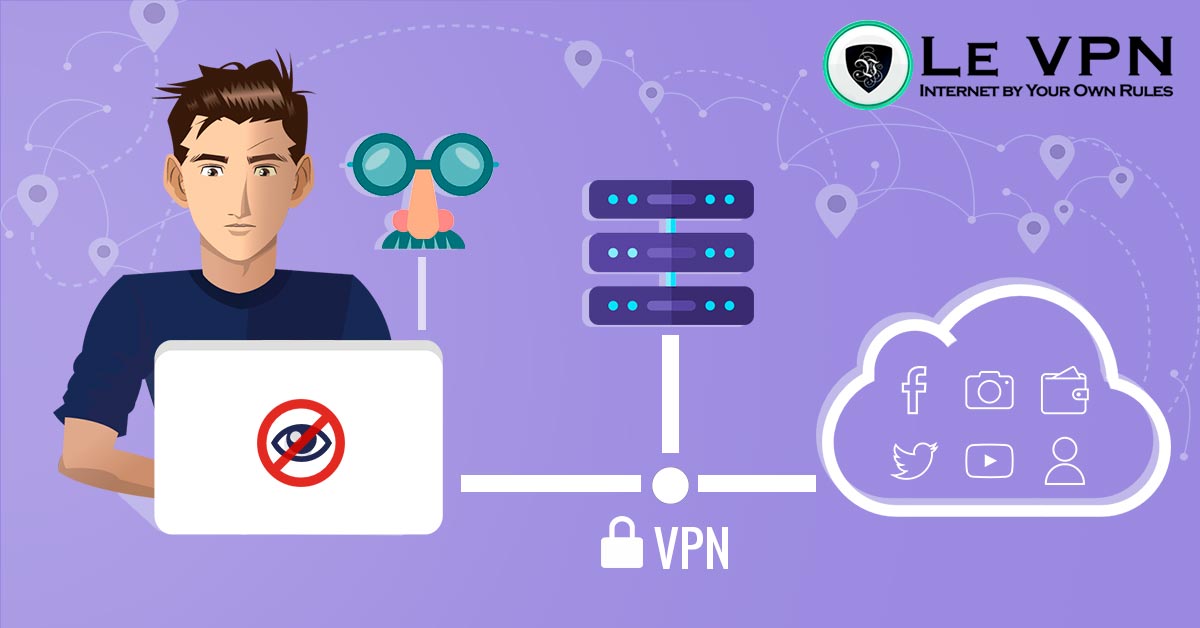
Personal Data Protection What Are Spoofing Attacks Le Vpn What if someone spoofed your bosses ip address and sent you a virus in an email? thankfully, there are several ways to protect your device from ip spoofing. regardless if you are a company or a private individual, you will want your general ip to be from a vpn and your true address to be hidden. Use a reliable vpn – a reputable vpn service encrypts your traffic and makes it difficult for hackers to monitor your activities online. vpns prevent hackers from spoofing your ip addresses, too. moreover, a reliable vpn protects you from compromised sites where the chances of ip spoofing are high.

Privacy Spotlight How Vpns Protect Your Data From Hackers And Your personal information is valuable. that’s why hackers and scammers try to steal it. follow this advice to protect the personal information on your devices and in your online accounts. To ensure you’re better prepared for such attacks, read on to learn about the most common types of spoofing, how to spot them, and what you can do to prevent them. Learn how spoofing attacks work, the tactics hackers use, and practical tips to protect your sensitive data from cyber threats. Ip spoofing lets attackers fake ip addresses to launch ddos, phishing & mitm attacks. learn how it works and how to prevent it with vpns, firewalls.

Phishing Protection What You Should Do And Don T Against Spoofing Learn how spoofing attacks work, the tactics hackers use, and practical tips to protect your sensitive data from cyber threats. Ip spoofing lets attackers fake ip addresses to launch ddos, phishing & mitm attacks. learn how it works and how to prevent it with vpns, firewalls. Understanding ip spoofing: ip spoofing is a malicious technique where attackers disguise their identity by sending packets from a fake ip address, leading to security breaches and data theft. Cybercrime always finds new and effective ways to violate network security and privacy protection systems in virtual contexts. one of these ways is spoofing or identity theft on the internet, a method increasingly used by hackers around the world. Learn what spoofing is, the different types of attacks, and how to protect yourself from cybercriminals impersonating trusted sources. Computing internet vpns attacks on vpns are unjustified and dangerous – and it's not how we achieve online safety opinion by george phillips published 17 hours ago.

How To Protect Your Data From Spoofing Attacks Fortra Email Security Understanding ip spoofing: ip spoofing is a malicious technique where attackers disguise their identity by sending packets from a fake ip address, leading to security breaches and data theft. Cybercrime always finds new and effective ways to violate network security and privacy protection systems in virtual contexts. one of these ways is spoofing or identity theft on the internet, a method increasingly used by hackers around the world. Learn what spoofing is, the different types of attacks, and how to protect yourself from cybercriminals impersonating trusted sources. Computing internet vpns attacks on vpns are unjustified and dangerous – and it's not how we achieve online safety opinion by george phillips published 17 hours ago.

Is Location Spoofing The Same As A Vpn Make Tech Easier Learn what spoofing is, the different types of attacks, and how to protect yourself from cybercriminals impersonating trusted sources. Computing internet vpns attacks on vpns are unjustified and dangerous – and it's not how we achieve online safety opinion by george phillips published 17 hours ago.
Comments are closed.