Protecting Your Organization From Volumetric Ddos Attack Cloudlayer8

5 Steps To Protecting Your Organization From A Ddos Attack Developed How to protect your organization from volumetric ddos attack. there are a number of ddos protection solutions available in the market. the quality and effectiveness varies based on type, prices and functionality. Our always on, cloud based ddos protection is built on an intuitive interface that empowers users to quickly and easily protect their internet properties against ddos attacks of any size or complexity in just a few clicks.

What Is A Ddos Attack Digital Attack Map How can the different firewall features help in defending against dos attacks and what steps can be taken to mitigate volumetric ddos attacks. Learn about the devastating impact of volumetric attacks, how they work, and how to protect your online assets. Cl8 can now provide subscription based, delivered and billed as a service ddos solutions aiming to relieve you from distributed denial of service volumetric attacks by mitigating the attack at its origin. Cl8 can now provide subscription based, delivered and billed as a service ddos solutions aiming to relieve you from distributed denial of service volumetric attacks.
Cloudflare Ddos Best Ddos Attack Protection Leyun Asia Cl8 can now provide subscription based, delivered and billed as a service ddos solutions aiming to relieve you from distributed denial of service volumetric attacks by mitigating the attack at its origin. Cl8 can now provide subscription based, delivered and billed as a service ddos solutions aiming to relieve you from distributed denial of service volumetric attacks. Mitigating and preventing volumetric attacks requires ddos protection technologies, such as remotely triggered blackholing (rtbh) and source based remotely triggered blackholing (s rtbh), which have proven to be very effective when used in a situationally appropriate manner. Ddos defence explained: how to detect and mitigate a ddos attack? ddos attacks are easier than ever to launch, harder to trace, and can cause real damage if you’re not prepared. the end result is typically the same: your users can’t reach you or your systems are unavailable. this article is a starting point. we’ll walk through what ddos actually is and how to detect one, how different. Ddos defense solutions help organizations identify and remediate active ddos attacks, as well as take proactive steps to prevent future attacks. Learn how volumetric ddos attacks overwhelm networks with high traffic volumes and discover strategies to protect your bandwidth.
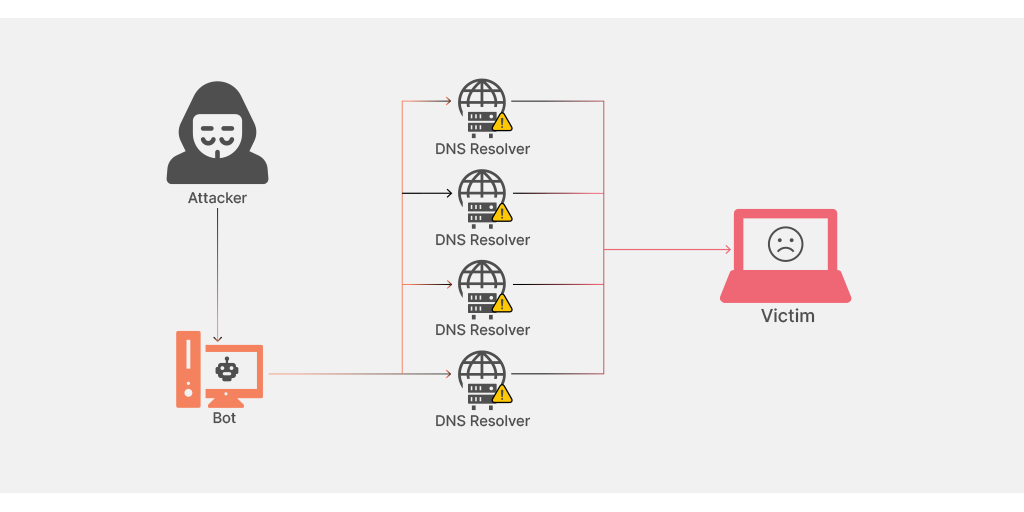
What Is A Ddos Attack Denial Of Service Attack Wpoven Mitigating and preventing volumetric attacks requires ddos protection technologies, such as remotely triggered blackholing (rtbh) and source based remotely triggered blackholing (s rtbh), which have proven to be very effective when used in a situationally appropriate manner. Ddos defence explained: how to detect and mitigate a ddos attack? ddos attacks are easier than ever to launch, harder to trace, and can cause real damage if you’re not prepared. the end result is typically the same: your users can’t reach you or your systems are unavailable. this article is a starting point. we’ll walk through what ddos actually is and how to detect one, how different. Ddos defense solutions help organizations identify and remediate active ddos attacks, as well as take proactive steps to prevent future attacks. Learn how volumetric ddos attacks overwhelm networks with high traffic volumes and discover strategies to protect your bandwidth.

464 Volumetric Attack Images Stock Photos 3d Objects Vectors Ddos defense solutions help organizations identify and remediate active ddos attacks, as well as take proactive steps to prevent future attacks. Learn how volumetric ddos attacks overwhelm networks with high traffic volumes and discover strategies to protect your bandwidth.
Comments are closed.