
Public Key And Private Key Cryptography Pdf Adventure Gold How do ssl & tls protect your data? confidentiality, integrity, authentication practical tls. asymmetric encryption requires two keys: a public key and a private key. these. When a client connects, the public and private keys work together during the key exchange: the public key is included in the certificate and sent to the client, who uses it to encrypt the pre master secret. the private key is kept secret. the server uses it to decrypt the pre master secret sent by the client.

What Is Public Key Cryptography Explained Simply Infographics How to explain public key cryptography and digital signatures to anyone. here’s an easy to understand analogy to help your non technical friends and customers understand public keys and private keys, and how they relate to cryptography and digital signatures. Public key encryption, digital signatures, key exchange certificates: bind a public key to an identity using a ca –used in tls to identify server (and possibly client). The ssl tls protocol uses a pair of keys – one private, one public – to authenticate, secure and manage secure connections. these keys are a linked pair of text files and are created together as a pair when you create your certificate signing request (csr). Encryption; public and private keys; how tls and ssl use cryptography preview; public key infrastructure (pki) rsa; diffie hellman; digital signature algorithm; module 2 review questions.
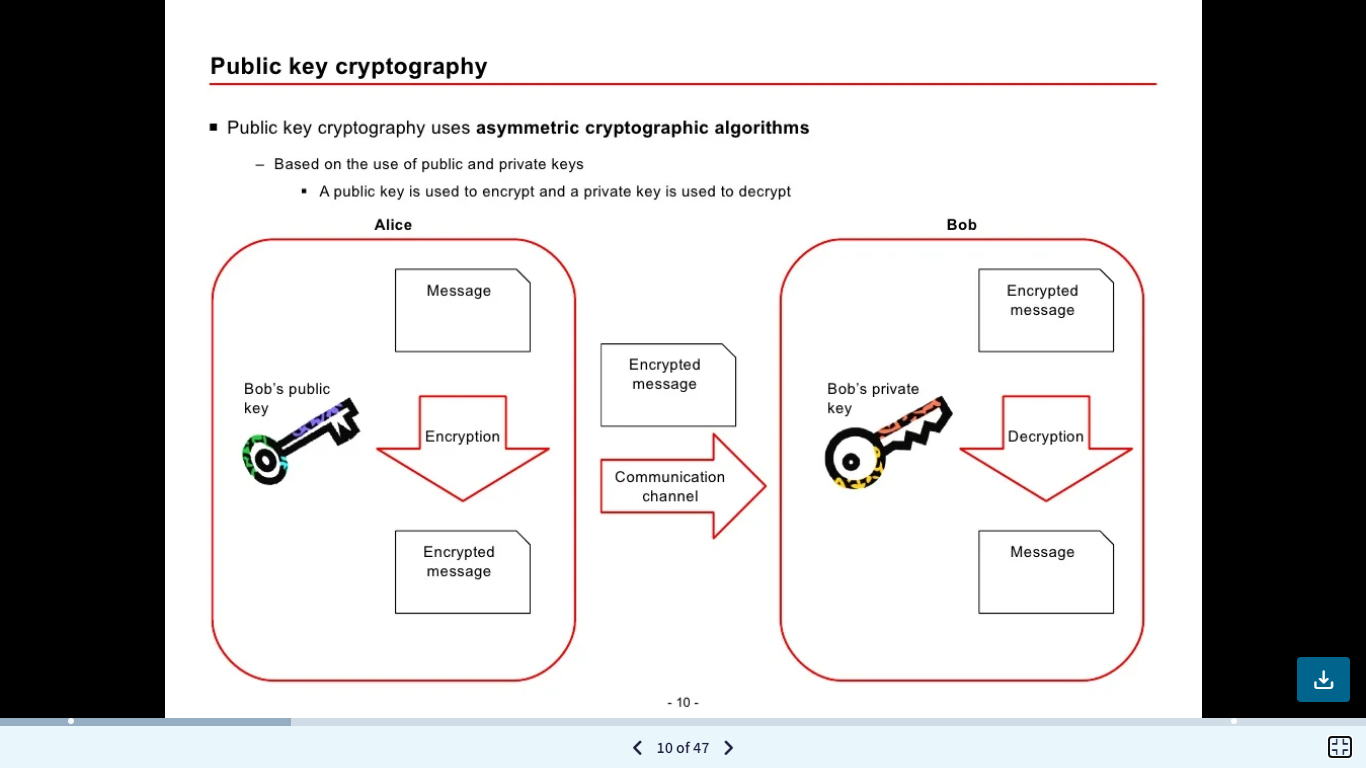
Solved Public Key Cryptography Public Key Cryptography Chegg The ssl tls protocol uses a pair of keys – one private, one public – to authenticate, secure and manage secure connections. these keys are a linked pair of text files and are created together as a pair when you create your certificate signing request (csr). Encryption; public and private keys; how tls and ssl use cryptography preview; public key infrastructure (pki) rsa; diffie hellman; digital signature algorithm; module 2 review questions. Public key cryptography, also known as asymmetric cryptography, is a fundamental concept in modern cryptography. at its core, public key cryptography utilizes a pair of keys public key and private key to encrypt and decrypt information. the public key is openly shared, while the private key is kept secret. It shows how individuals securely exchange data using public and private keys, encrypting messages with the recipient's public key and decrypting with their private key. additionally, it touches on message signing for authentication and integrity verification, and demonstrates hybrid encryption combining asymmetric and symmetric. We construct the first truly practical signature scheme with tight security in a real world multi user setting with adaptive corruptions. the scheme is based on a new way of applying the fiat shamir approach to construct tightly secure signatures from certain identification schemes. Public key cryptography designates the class of cryptographic algorithms that includes asymmetric encryption (and its cousin key exchange) and digital signatures. in these algorithms, there are two operations that correspond to each other (encrypt > decrypt, or sign > verify) with the characteristic that one of the operations can be done by.

Toan N On Linkedin Public And Private Keys Signatures Key Public key cryptography, also known as asymmetric cryptography, is a fundamental concept in modern cryptography. at its core, public key cryptography utilizes a pair of keys public key and private key to encrypt and decrypt information. the public key is openly shared, while the private key is kept secret. It shows how individuals securely exchange data using public and private keys, encrypting messages with the recipient's public key and decrypting with their private key. additionally, it touches on message signing for authentication and integrity verification, and demonstrates hybrid encryption combining asymmetric and symmetric. We construct the first truly practical signature scheme with tight security in a real world multi user setting with adaptive corruptions. the scheme is based on a new way of applying the fiat shamir approach to construct tightly secure signatures from certain identification schemes. Public key cryptography designates the class of cryptographic algorithms that includes asymmetric encryption (and its cousin key exchange) and digital signatures. in these algorithms, there are two operations that correspond to each other (encrypt > decrypt, or sign > verify) with the characteristic that one of the operations can be done by.
