What Is Sql Injection
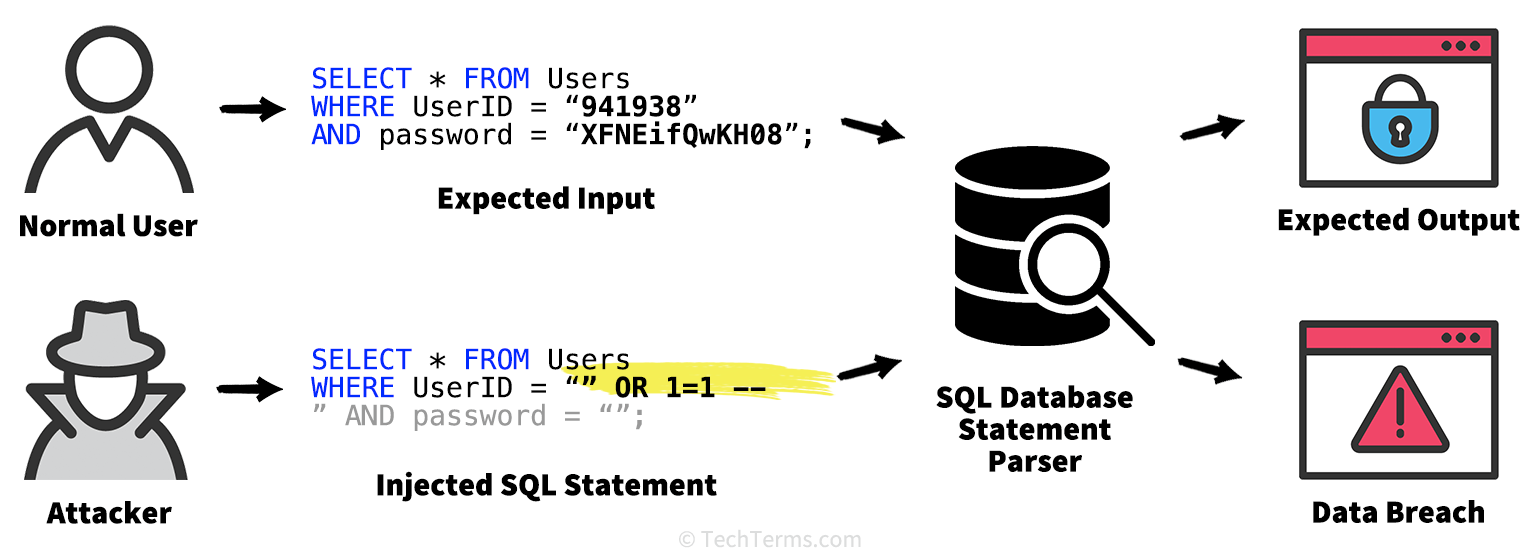
Sql Injection Definition Sql injection is a vulnerability that happens when an application builds database queries from user input without safely separating data from code. an attacker sends input that changes the intended sql query. Sql injection is a code injection technique used to attack data driven applications, by inserting malicious sql statements into an entry field for execution. learn how sql injection works, its root causes, its types, and its history from this article.

What Is Sql Injection Attack Example Prevention Gridinsoft Sql injection is a security vulnerability that allows attackers to manipulate databases by injecting malicious sql code into web applications. learn how sql injection works, what are its consequences, and how to protect your web applications and data from this threat. Sql injection (sqli) is a cyberattack where malicious sql code is injected into vulnerable web applications. this allows attackers to interfere with database queries and manipulate them to gain. Sql injection (often abbreviated as sqli) is a cyber threat that targets applications that use sql (structured query language) databases. Sql injection is an attack in which malicious code is inserted into strings that are later passed to an instance of the sql server database engine for parsing and execution.

Sql Injection For Beginners Understanding The Basics Sql injection (often abbreviated as sqli) is a cyber threat that targets applications that use sql (structured query language) databases. Sql injection is an attack in which malicious code is inserted into strings that are later passed to an instance of the sql server database engine for parsing and execution. Sql injection is a type of attack that exploits vulnerabilities in an application's code by inserting an sql query into regular input or form fields. learn how sql injection works, what are the types and examples of sql injection, and how to prevent these attacks with input validation, filtering, and web application firewall. What is a sql injection attack exactly, and is your organization at risk? here's what you need to know and how to protect your company from attacks. Learn how sql injection in cyber security threatens your data. discover prevention strategies, attack types, and best practices to secure web applications. Sql injection is a major concern when developing a web application. it occurs when the application accepts a malicious user input and then uses it as a part of sql statement to query a backend database.

Sql Injection True Sparrow Blog Sql injection is a type of attack that exploits vulnerabilities in an application's code by inserting an sql query into regular input or form fields. learn how sql injection works, what are the types and examples of sql injection, and how to prevent these attacks with input validation, filtering, and web application firewall. What is a sql injection attack exactly, and is your organization at risk? here's what you need to know and how to protect your company from attacks. Learn how sql injection in cyber security threatens your data. discover prevention strategies, attack types, and best practices to secure web applications. Sql injection is a major concern when developing a web application. it occurs when the application accepts a malicious user input and then uses it as a part of sql statement to query a backend database.

Sql Injection What Is It The Security Blog From Loaris Learn how sql injection in cyber security threatens your data. discover prevention strategies, attack types, and best practices to secure web applications. Sql injection is a major concern when developing a web application. it occurs when the application accepts a malicious user input and then uses it as a part of sql statement to query a backend database.
Comments are closed.