Telecom Cyber Attacks Arkose Labs
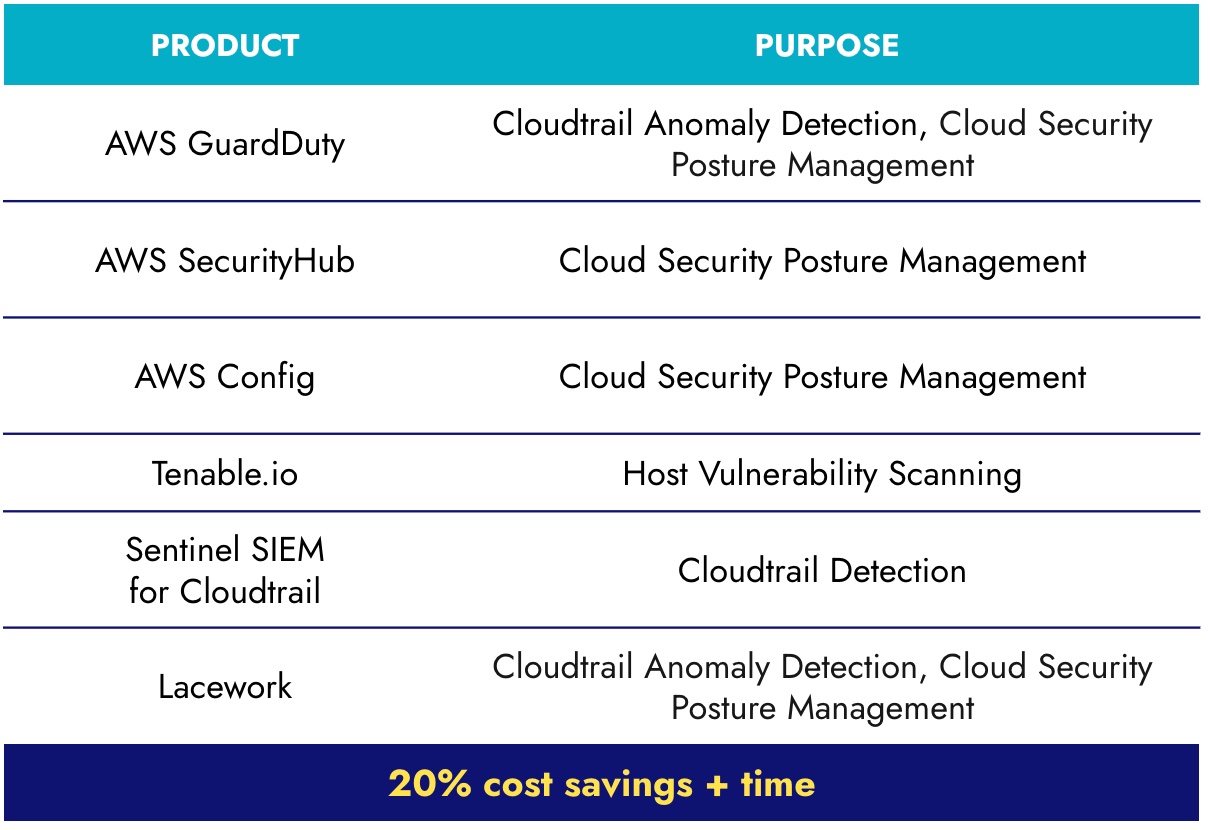
Arkose Labs Beats The Bots With 6 To 1 Tool Consolidation And 20 Cost Telecom networks can be vulnerable to cyberattacks, specifically session hijacking and man in the middle (mitm) attacks. these attacks can compromise both network security and that of user accounts. The analysis reveals where attacks originate, the industries targeted and the techniques used: the top countries of origin of attacks: united states, vietnam, great britain, germany and.

How Arkose Labs Built A Toolkit To Fight Fraud Aws Startups Blog By proactively defending against these attacks, companies are able to ensure their customers’ security without compromising a good user experience. businesses can incorporate arkose labs into any touchpoint to detect fraudulent traffic, such as login flow or new account registration. Arkose labs analyses traffic against signs of malicious intent to distinguish automated and human attackers from good users. its ai powered platform combines risk assessments with dynamic attack response that undermines the roi behind attacks while improving good user throughput. The need for telecom services, as well as their prominence in our day to day lives as critical infrastructure, have made the industry a prime target for cyberattacks. These exercises are performed to expose city staff to various attack vectors and possible attack interdiction techniques before they are needed to defend city information assets and resources.

Cyber Attacks Articles Biography Entrepreneur The need for telecom services, as well as their prominence in our day to day lives as critical infrastructure, have made the industry a prime target for cyberattacks. These exercises are performed to expose city staff to various attack vectors and possible attack interdiction techniques before they are needed to defend city information assets and resources. Drawing on a full year of scammer behavioral data, the report does not merely outline patterns of malicious activity—it deconstructs the economics and strategy behind a now mature criminal ecosystem. The report focuses on attacks from fraud outlets that combine state of the art technology with stolen identity credentials and human efforts. Secure your telco network and customer accounts with arkose labs. combat evolving cyber threats like atos, sim swaps and fraud while protecting revenue and trust. Researchers assessed the attacks across three primary attack vectors: basic bots, intelligent bots, and human fraud farms. fraudsters use these vectors to launch attack types such as sms toll.
Telecom Cyber Attacks Popularity In 2021 Cognyte Drawing on a full year of scammer behavioral data, the report does not merely outline patterns of malicious activity—it deconstructs the economics and strategy behind a now mature criminal ecosystem. The report focuses on attacks from fraud outlets that combine state of the art technology with stolen identity credentials and human efforts. Secure your telco network and customer accounts with arkose labs. combat evolving cyber threats like atos, sim swaps and fraud while protecting revenue and trust. Researchers assessed the attacks across three primary attack vectors: basic bots, intelligent bots, and human fraud farms. fraudsters use these vectors to launch attack types such as sms toll.
Rise Of The Cyborg Arkose Labs Fraud Report Finds Secure your telco network and customer accounts with arkose labs. combat evolving cyber threats like atos, sim swaps and fraud while protecting revenue and trust. Researchers assessed the attacks across three primary attack vectors: basic bots, intelligent bots, and human fraud farms. fraudsters use these vectors to launch attack types such as sms toll.

Arkose Labs Report Finds Nearly Three Quarters Of Web Traffic Is
Comments are closed.