
The 4 Main Types Of Spoofing Attacks And How To Preve Vrogue Co Here are the four most common ones. 1. email spoofing. let's say you receive an email claiming to be from your bank, and it says that you need to log in to your online banking account and change your password. In this article, we will explore the four main types of spoofing attacks and discuss ways to prevent them. types of spoofing attacks. ip spoofing; ip spoofing is a type of attack where an attacker sends packets from a false (or "spoofed") ip address in order to disguise their identity.
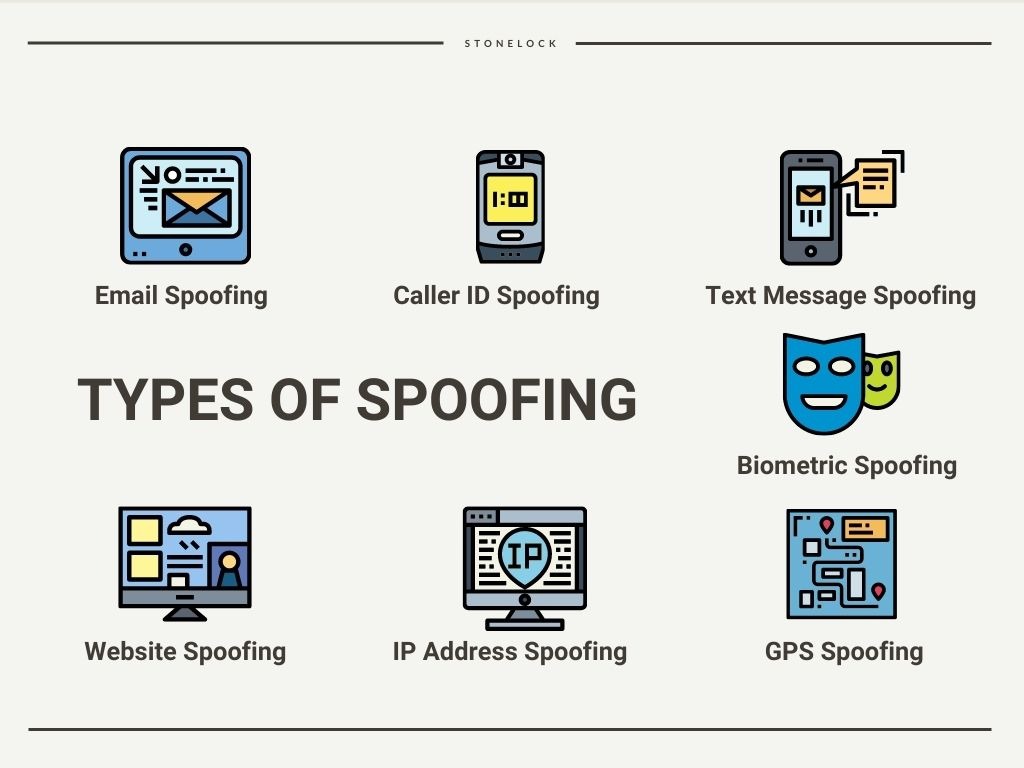
How To Prevent Spoofing Attacks And Understand The Ma Vrogue Co A spoofing attack is a type of cyberattack where an attacker impersonates another device, user, or service to deceive, gain unauthorized access, or disrupt systems and communications. spoofing attacks exploit the trust established between legitimate entities, making it challenging for victims to identify malicious activity. In this section, we’ll explore 12 common types of spoofing, complete with real life examples to help you recognize and avoid these threats. 1. email spoofing is when cybercriminals send bogus emails to deceive recipients using email addresses that appear nearly identical to trusted organizations or contacts. These are just 4 of the most common types of spoofing attacks. there are many more, though, including arp spoofing, dns spoofing, gps spoofing, and so on. the only surefire way to prevent spoofing attacks is to be exhaustive and rigorous with authentication measures and implementation. this may include:. Learn about spoofing attacks like email, ip, and website spoofing. understand their risks and discover prevention measures to stay protected.

Spoofing Understanding Types Prevention Methods Fourtrezz These are just 4 of the most common types of spoofing attacks. there are many more, though, including arp spoofing, dns spoofing, gps spoofing, and so on. the only surefire way to prevent spoofing attacks is to be exhaustive and rigorous with authentication measures and implementation. this may include:. Learn about spoofing attacks like email, ip, and website spoofing. understand their risks and discover prevention measures to stay protected. Below, we outline the most common types of spoofing attacks, how they work, and how to recognize them. email spoofing: fraudulent emails that look like they come from trusted contacts. caller id spoofing: fake phone calls from legitimate looking numbers. ip spoofing: hiding the real origin of cyberattacks. Understanding the types and risks of spoofing is crucial to mitigating its impact. spoofing comes in various forms, each targeting different communication channels to deceive victims. here are the most common types of spoofing attacks you should be aware of. 1. email spoofing. In the realm of digital security, a spoofing attack is a type of cyber threat where an attacker impersonates a trusted entity, such as an individual, device, or system, to deceive its target. by masquerading as a legitimate source, attackers gain unauthorized access to sensitive information, manipulate data, or perform other malicious actions. The lesson explains four types of spoofing attacks: arp spoofing attacks, dns server spoofing attacks, ip address spoofing attacks, and mac address spoofing attacks.

Top 10 Types Of Spoofing Attacks And How To Protect Your Data Tech Below, we outline the most common types of spoofing attacks, how they work, and how to recognize them. email spoofing: fraudulent emails that look like they come from trusted contacts. caller id spoofing: fake phone calls from legitimate looking numbers. ip spoofing: hiding the real origin of cyberattacks. Understanding the types and risks of spoofing is crucial to mitigating its impact. spoofing comes in various forms, each targeting different communication channels to deceive victims. here are the most common types of spoofing attacks you should be aware of. 1. email spoofing. In the realm of digital security, a spoofing attack is a type of cyber threat where an attacker impersonates a trusted entity, such as an individual, device, or system, to deceive its target. by masquerading as a legitimate source, attackers gain unauthorized access to sensitive information, manipulate data, or perform other malicious actions. The lesson explains four types of spoofing attacks: arp spoofing attacks, dns server spoofing attacks, ip address spoofing attacks, and mac address spoofing attacks.

Top Types Of Spoofing Attacks Gridinsoft Blogs In the realm of digital security, a spoofing attack is a type of cyber threat where an attacker impersonates a trusted entity, such as an individual, device, or system, to deceive its target. by masquerading as a legitimate source, attackers gain unauthorized access to sensitive information, manipulate data, or perform other malicious actions. The lesson explains four types of spoofing attacks: arp spoofing attacks, dns server spoofing attacks, ip address spoofing attacks, and mac address spoofing attacks.
