The Threat Hunting Reference Model Part 1 The Hunting Maturity Model
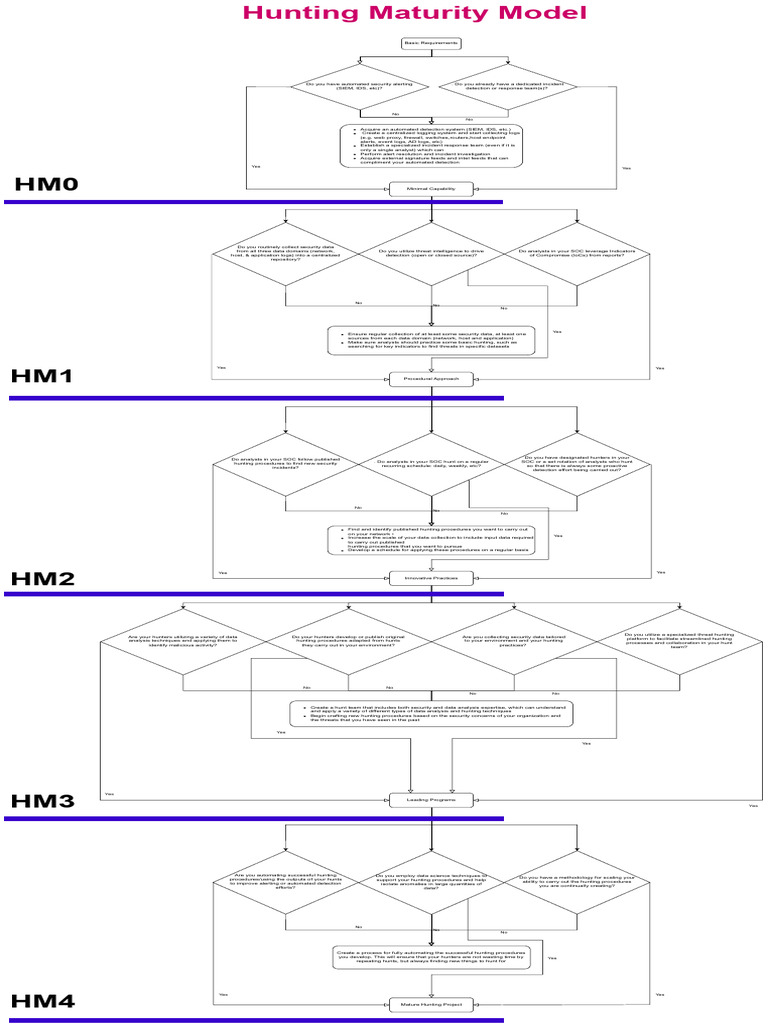
Hunting Maturity Model V 01 Pdf Computer Science Information Science A maturity model will ideally help anyone thinking of getting into hunting get a good idea of what an appropriate initial capability would be. more importantly for those organizations who already hunt, the hmm can be used both to measure their current maturity and provide a roadmap for improvement. hunt. The hunting maturity model, developed by sqrrl's security architect and hunter david bianco, describes five levels of organizational hunting capability, ranging from hmm0 (the least.

The Threat Hunting Reference Model Part 3 The Hunt Matrix Sqrrl The hunting maturity model (hmm) is a simple model for evaluating an organization's threat hunting capability. it provides not only a "where are we now?" metric, but also a roadmap for program improvement. The threat hunting maturity model defines the organizations’ capabilities of effective cyber hunting and threat response. the more capable the business is, the higher the hunting maturity model (hmm) level is, where the hmm0 is the least capable and the hmm4 is the most efficient. Four stages make up a model process for successful hunting. the hunting loop illustrates that h. nting is most effective when it’s habitual and adaptable. let’s break it down step by step, beginning wit. hunting starting points, or what we call “trailheads”: hunt starts with creating a hypothesis , or an educated guess, about some typ. Before moving forward in describing the threat hunting maturity model, we need to understand what threat hunting is. threat hunting is the act of proactively and iteratively searching a network to detect and isolate advanced threats that exploit organizations’ existing security mechanisms.

Enterprise Detection Response A Simple Hunting Maturity Model Four stages make up a model process for successful hunting. the hunting loop illustrates that h. nting is most effective when it’s habitual and adaptable. let’s break it down step by step, beginning wit. hunting starting points, or what we call “trailheads”: hunt starts with creating a hypothesis , or an educated guess, about some typ. Before moving forward in describing the threat hunting maturity model, we need to understand what threat hunting is. threat hunting is the act of proactively and iteratively searching a network to detect and isolate advanced threats that exploit organizations’ existing security mechanisms. In this four part series we’ll be looking at team cymru’s threat hunting maturity model. its purpose is to define each step of the journey that organizations take to hire, empower and gain value from an elite threat hunting team. The threat hunting maturity model (hmm) is a framework that helps organizations improve their threat hunting skills and strengthen their defenses against evolving cyber threats. these threats are growing more complex every year, and organizations are under increasing pressure to stay ahead of attackers. the fbi's 2024 internet crime report (published in april 2025) highlights the scale of the. In this article, i’ve gathered a selection of threat hunting frameworks that have shaped the field. some are community born, others come from leading cybersecurity vendors, and a few are still under the radar gems. Going beyond passive security tools, threat hunting involves actively looking for potential threats, making it one of the most powerful defense mechanisms.

The Threat Hunting Reference Model Part 1 Measuring Hunting Maturity In this four part series we’ll be looking at team cymru’s threat hunting maturity model. its purpose is to define each step of the journey that organizations take to hire, empower and gain value from an elite threat hunting team. The threat hunting maturity model (hmm) is a framework that helps organizations improve their threat hunting skills and strengthen their defenses against evolving cyber threats. these threats are growing more complex every year, and organizations are under increasing pressure to stay ahead of attackers. the fbi's 2024 internet crime report (published in april 2025) highlights the scale of the. In this article, i’ve gathered a selection of threat hunting frameworks that have shaped the field. some are community born, others come from leading cybersecurity vendors, and a few are still under the radar gems. Going beyond passive security tools, threat hunting involves actively looking for potential threats, making it one of the most powerful defense mechanisms.
Comments are closed.