What Is Email Spoofing And How Can You Protect Yourself
What Is Email Spoofing And How Can You Protect Yourself 1password Email spoofing is an attack where hackers make it appear that an email originates from a different address than it does. spoofing allows the attacker to impersonate people or organizations for various reasons. In this article, you’ll find everything you need to know about email spoofing what it is, the reasons behind it, and how to deal with it. use a secure email provider.

Email Spoofing 101 And How Can You Protect Yourself From Attackers Someone could be using email spoofing to mask their true identity and trick you into compromising your security. discover what email spoofing is, how it works, and how to spot a spoofed email. then get norton 360 deluxe to help protect against malicious email attachments and links. Learn how email spoofing works and how to protect yourself. every day, businesses and individuals send and receive countless emails. but what if some of those emails weren’t actually from the people they appeared to be from?. Email spoofing is a rising threat, where attackers forge an email’s sender address to appear as a trusted source. this tactic underpins many cyberattacks, from phishing to business email compromise (bec), and it can have devastating consequences for both organizations and individuals. Understanding email spoofing is crucial for your online safety. learn what email spoofing is, how to identify suspicious messages, and implement protection measures against this deceptive tactic.
Email Spoofing What Is It How To Protect Yourself Email spoofing is a rising threat, where attackers forge an email’s sender address to appear as a trusted source. this tactic underpins many cyberattacks, from phishing to business email compromise (bec), and it can have devastating consequences for both organizations and individuals. Understanding email spoofing is crucial for your online safety. learn what email spoofing is, how to identify suspicious messages, and implement protection measures against this deceptive tactic. How does email spoofing work, what are its consequences and most importantly, how can you protect yourself from it? we’ll tell you everything in this article. Users should be aware of malicious links, email phishing or spear phishing, and email spoofing to best protect themselves. in this article, we’ll explore email spoofing, why it’s a problem, and how to protect yourself by preventing spoofed emails from getting to you. In this article, we will explore what email spoofing is, how it works, its role in phishing attack s, and the steps individuals and organisations can take to protect themselves from falling victim to such threats. what is email spoofing?. Learn how email spoofing can compromise your personal or sensitive information and actions you can take to protect yourself.

Email Spoofing Scams What You Need To Know To Protect Yourself Seqrex How does email spoofing work, what are its consequences and most importantly, how can you protect yourself from it? we’ll tell you everything in this article. Users should be aware of malicious links, email phishing or spear phishing, and email spoofing to best protect themselves. in this article, we’ll explore email spoofing, why it’s a problem, and how to protect yourself by preventing spoofed emails from getting to you. In this article, we will explore what email spoofing is, how it works, its role in phishing attack s, and the steps individuals and organisations can take to protect themselves from falling victim to such threats. what is email spoofing?. Learn how email spoofing can compromise your personal or sensitive information and actions you can take to protect yourself.
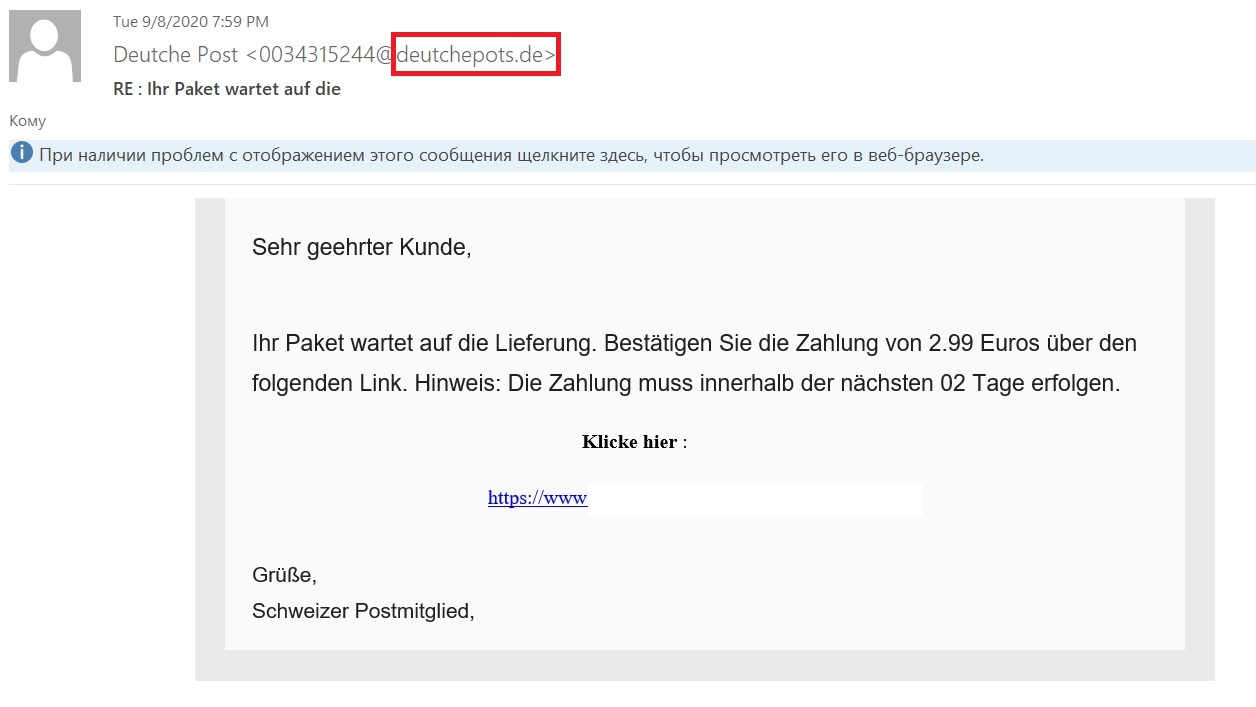
What Is Email Spoofing How To Protect Yourself In this article, we will explore what email spoofing is, how it works, its role in phishing attack s, and the steps individuals and organisations can take to protect themselves from falling victim to such threats. what is email spoofing?. Learn how email spoofing can compromise your personal or sensitive information and actions you can take to protect yourself.
Comments are closed.