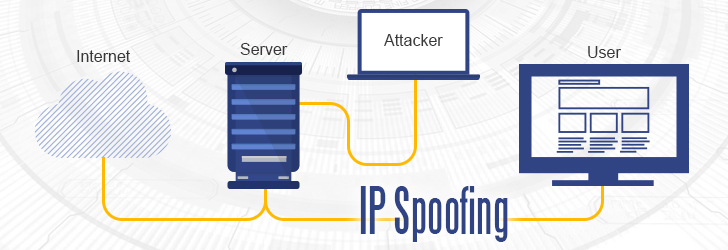
Ip Spoofing Ip spoofing is a technique often used by attackers to launch distributed denial of service attacks and man in the middle attacks against targeted devices or the surrounding infrastructures. the goal of ddos attacks is to overwhelm a target with traffic while hiding the identity of the malicious source, preventing mitigation efforts. What is ip spoofing? ip spoofing is the creation of internet protocol (ip) packets which have a modified source address in order to either hide the identity of the sender, to impersonate another computer system, or both.

Ip Spoofing How It Works Types Examples Why Is Important Techpeal In computer networking, ip address spoofing or ip spoofing is the creation of internet protocol (ip) packets with a false source ip address, for the purpose of impersonating another computing system. [1] the basic protocol for sending data over the internet network and many other computer networks is the internet protocol (ip). With ip spoofing, intruder sends message to a computer system with an ip address indicating message is coming from a different ip address than its actually coming from. if intent is to gain unauthorized access, then spoof ip address will be that of a system the target considers a trusted host. Url spoofing – this is commonly known as website spoofing. the approach is simple yet very lethal and convincing. what the attacker does in this case is to leverage on certain things like error in url spelling (typo squatting) that victims may make when looking for trusted websites on search engines. Ip spoofing, or ip address spoofing, refers to the creation of internet protocol (ip) packets with a false source ip address to impersonate another computer system. ip spoofing allows cybercriminals to carry out malicious actions, often without detection.
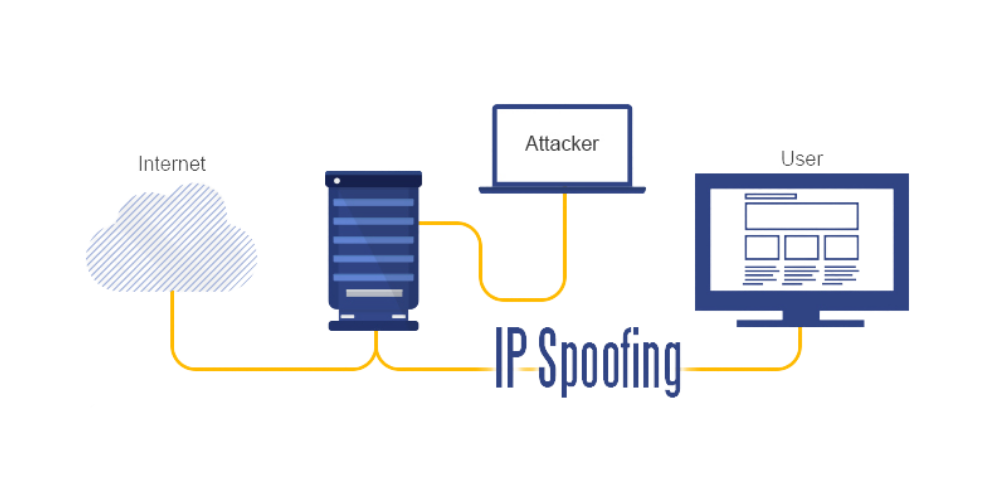
Ip Spoofing What Is Ip Spoofing Attack Gridinsoft Blogs Url spoofing – this is commonly known as website spoofing. the approach is simple yet very lethal and convincing. what the attacker does in this case is to leverage on certain things like error in url spelling (typo squatting) that victims may make when looking for trusted websites on search engines. Ip spoofing, or ip address spoofing, refers to the creation of internet protocol (ip) packets with a false source ip address to impersonate another computer system. ip spoofing allows cybercriminals to carry out malicious actions, often without detection. Ip address spoofing is the act of falsifying the content in the source ip header, usually with randomized numbers, either to mask the sender’s identity or to launch a reflected ddos attack, as described below. Ip spoofing or ip address spoofing is a technique in which a malicious ip packet is spoofed as legitimate by modifying the source ip address in the packet's header, making it appear as though the packet originates from a trusted device within the network. Ip spoofing is a method in which tcp ip or udp ip data packets are sent with a fake sender address. the attacker uses the address of an authorized, trustworthy system. in this way, it can inject its own packets into the foreign system that would otherwise be blocked by a filter system. Ip spoofing lets attackers fake ip addresses to launch ddos, phishing & mitm attacks. learn how it works and how to prevent it with vpns, firewalls.
Ip Spoofing Attack Explanation Protection Gridinsoft Blogs Ip address spoofing is the act of falsifying the content in the source ip header, usually with randomized numbers, either to mask the sender’s identity or to launch a reflected ddos attack, as described below. Ip spoofing or ip address spoofing is a technique in which a malicious ip packet is spoofed as legitimate by modifying the source ip address in the packet's header, making it appear as though the packet originates from a trusted device within the network. Ip spoofing is a method in which tcp ip or udp ip data packets are sent with a fake sender address. the attacker uses the address of an authorized, trustworthy system. in this way, it can inject its own packets into the foreign system that would otherwise be blocked by a filter system. Ip spoofing lets attackers fake ip addresses to launch ddos, phishing & mitm attacks. learn how it works and how to prevent it with vpns, firewalls.
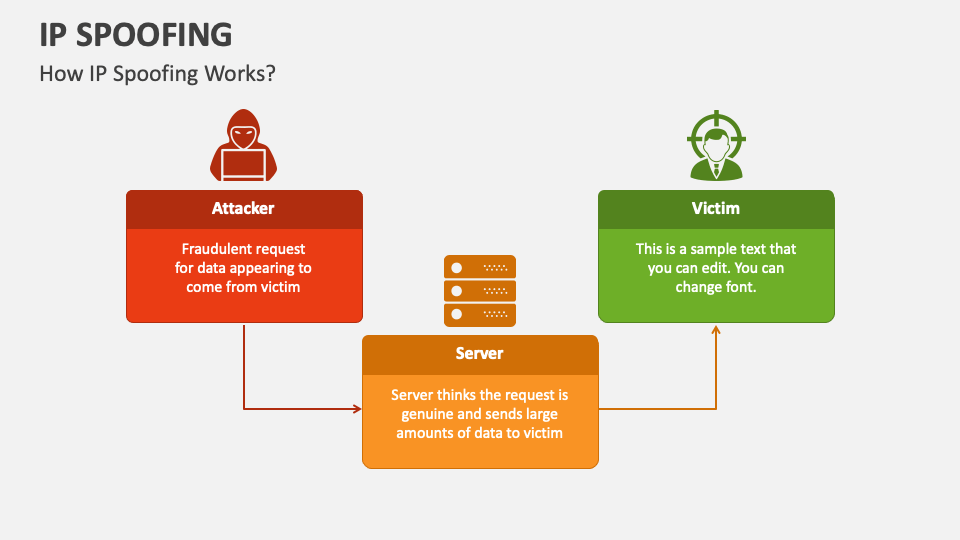
Ip Spoofing Powerpoint And Google Slides Template Ppt Slides Ip spoofing is a method in which tcp ip or udp ip data packets are sent with a fake sender address. the attacker uses the address of an authorized, trustworthy system. in this way, it can inject its own packets into the foreign system that would otherwise be blocked by a filter system. Ip spoofing lets attackers fake ip addresses to launch ddos, phishing & mitm attacks. learn how it works and how to prevent it with vpns, firewalls.
