
Role Based Access Control Rbac Role Based Access Control Rbac By Role based access control (rbac) is a model for authorizing end user access to systems, applications and data based on a user’s predefined role. Role based access control (rbac) is a security methodology based on managing user access to protect resources, including data, applications, and systems, from improper access, modification, addition, or deletion. it grants access based on a user’s needs according to their position.

What Is Role Based Access Control Rbac Pdf Computer Access Role based access control (rbac) is a method of managing user access to systems, networks, or resources based on their role within a team or a larger organization. Role based access control (rbac), or role based security, is an industry leading solution with multiple benefits. it is a feature of network access control (nac) and assigns permissions and grants access based on a user’s role within an organization. how does rbac work?. Role based access control (rbac) is a must have for securing access in today’s dynamic, cloud native world in the cloud, workloads spin up and down constantly, containers are ephemeral, and permissions can get out of control fast instead of manually managing who gets access to what (which is a nightmare at scale), rbac groups permissions into roles—like “dev,” “ops,” or. Role based access control (rbac) is a security, governance, and compliance model that restricts system or data access based on predefined roles within an organization. instead of assigning permissions directly to each user, rbac enables administrators to create role profiles—each encapsulating a set of access rights—and assign them to users.
.png?width=687&name=RBAC_blog_diagram (2).png)
Role Based Access Control Rbac Role based access control (rbac) is a must have for securing access in today’s dynamic, cloud native world in the cloud, workloads spin up and down constantly, containers are ephemeral, and permissions can get out of control fast instead of manually managing who gets access to what (which is a nightmare at scale), rbac groups permissions into roles—like “dev,” “ops,” or. Role based access control (rbac) is a security, governance, and compliance model that restricts system or data access based on predefined roles within an organization. instead of assigning permissions directly to each user, rbac enables administrators to create role profiles—each encapsulating a set of access rights—and assign them to users. The term role based access control (rbac) refers to an authorization strategy that organizes privileges based on a role (hence the 'role based' prefix). the rbac authorization strategy is commonly used by medium sized to large organizations that need to categorize their personnel using role assignment. Role based access control (rbac) ensures that only authorized users can access objects and perform operations. role based access control is defined as a set of rules that govern and restrict user access to operations and objects based on their identity, intent, and session attributes. Role based access control (rbac) is a method of restricting network access based on the roles of individual users within an enterprise. organizations use rbac also called role based security to parse levels of access based on an employee's roles and responsibilities. Role based access control (rbac) is a method of protecting sensitive data from improper access, modification, addition, or deletion. it allows employees to have access to the information required to fulfill their responsibilities.
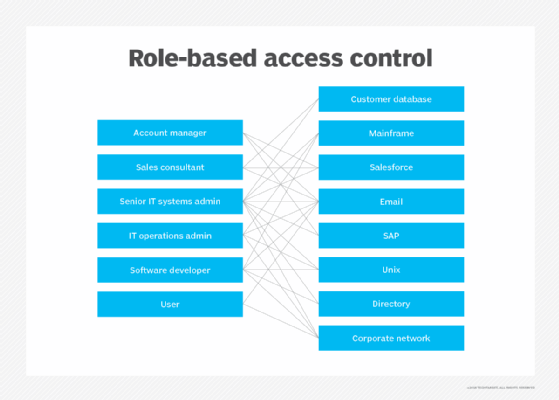
What Is Role Based Access Control Rbac Definition From Whatis The term role based access control (rbac) refers to an authorization strategy that organizes privileges based on a role (hence the 'role based' prefix). the rbac authorization strategy is commonly used by medium sized to large organizations that need to categorize their personnel using role assignment. Role based access control (rbac) ensures that only authorized users can access objects and perform operations. role based access control is defined as a set of rules that govern and restrict user access to operations and objects based on their identity, intent, and session attributes. Role based access control (rbac) is a method of restricting network access based on the roles of individual users within an enterprise. organizations use rbac also called role based security to parse levels of access based on an employee's roles and responsibilities. Role based access control (rbac) is a method of protecting sensitive data from improper access, modification, addition, or deletion. it allows employees to have access to the information required to fulfill their responsibilities.
