What Is Spoofing Email Ip Other Spoofing Definition
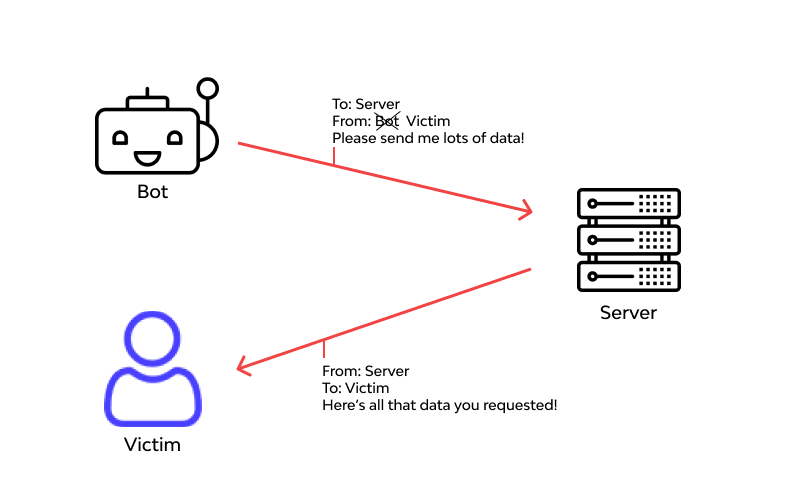
What Is Ip Spoofing Definition Types Protection Spoofing is when someone disguises an email address, sender name, phone number, or website url—often just by changing one letter, symbol, or number—to convince you that you are interacting with a. Spoofing is when a scammer disguises themselves as someone you trust in order to steal your identity. for example, if you’re a best buy customer, you might receive fake emails about subscriptions you never signed up for or geek squad renewals.

What Is Ip Spoofing Definition Types Protection Spoofing is the act of falsifying information to impersonate a trusted source, often to steal data or money. learn more about spoofing here. Spoofing is one of the most common tactics used by cybercriminals, which includes brand impersonation and forged credentials aimed at obtaining user’s information. a recent study shows that 61% of phishing attacks employed fake microsoft login pages to capture enterprise credentials. it is crucial for organizations to understand what is spoofing in order to ensure that its vital information. Spoofing is a broad term for the type of behavior that involves a cybercriminal masquerading as a trusted entity or device to get you to do something beneficial to the hacker — and detrimental to you. any time an online scammer disguises their identity as something else, it’s spoofing. Learn what is spoofing, its types, risks, and how to stay safe from this deceptive cyber threat with these essential tips.

What Is Ip Spoofing Definition Types Protection Spoofing is a broad term for the type of behavior that involves a cybercriminal masquerading as a trusted entity or device to get you to do something beneficial to the hacker — and detrimental to you. any time an online scammer disguises their identity as something else, it’s spoofing. Learn what is spoofing, its types, risks, and how to stay safe from this deceptive cyber threat with these essential tips. Learn the spoofing definition and understand what spoofing is in cyber security. this article explains spoofing attacks, types of spoofing, how spoofers work, and provides examples such as email, caller id, and dns spoofing. Learn what is a spoofer, how spoofing attacks work, and how to prevent spoofing in cybersecurity. includes real world examples and prevention tips. A growing number of users are looking for ways to control their digital identity. this leads to a key question: what is a spoofer? in simple terms, a spoofer is a method, tool, or technique used to forge or fake data such as ip addresses, browser fingerprints, user agents, or device information. this article explains what spoofing is, common spoofing methods, its applications, and associated. Spoofing is a cyberattack technique that tricks users into interacting with malicious it systems. cybercriminals disguise malicious assets — like emails, website login pages, or dns records — to look like genuine ones.
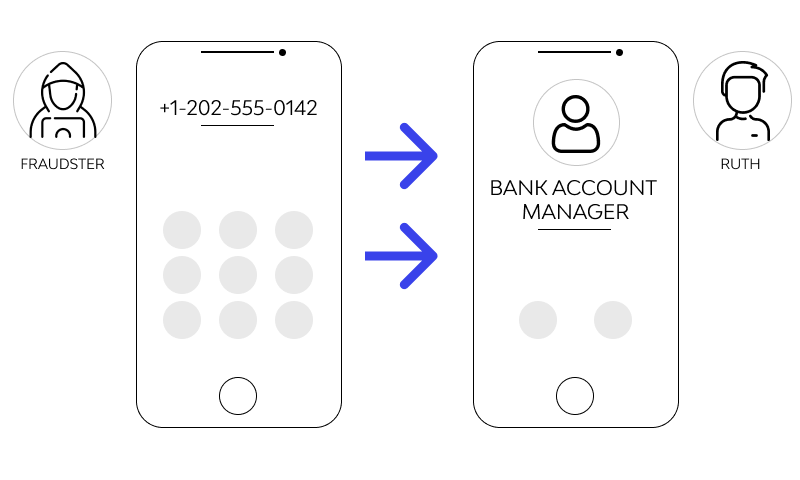
What Is Ip Spoofing Definition Types Protection Learn the spoofing definition and understand what spoofing is in cyber security. this article explains spoofing attacks, types of spoofing, how spoofers work, and provides examples such as email, caller id, and dns spoofing. Learn what is a spoofer, how spoofing attacks work, and how to prevent spoofing in cybersecurity. includes real world examples and prevention tips. A growing number of users are looking for ways to control their digital identity. this leads to a key question: what is a spoofer? in simple terms, a spoofer is a method, tool, or technique used to forge or fake data such as ip addresses, browser fingerprints, user agents, or device information. this article explains what spoofing is, common spoofing methods, its applications, and associated. Spoofing is a cyberattack technique that tricks users into interacting with malicious it systems. cybercriminals disguise malicious assets — like emails, website login pages, or dns records — to look like genuine ones.

What Is Ip Address Spoofing Attack Definition Anti Spoofing Www Vrogue Co A growing number of users are looking for ways to control their digital identity. this leads to a key question: what is a spoofer? in simple terms, a spoofer is a method, tool, or technique used to forge or fake data such as ip addresses, browser fingerprints, user agents, or device information. this article explains what spoofing is, common spoofing methods, its applications, and associated. Spoofing is a cyberattack technique that tricks users into interacting with malicious it systems. cybercriminals disguise malicious assets — like emails, website login pages, or dns records — to look like genuine ones.
Comments are closed.