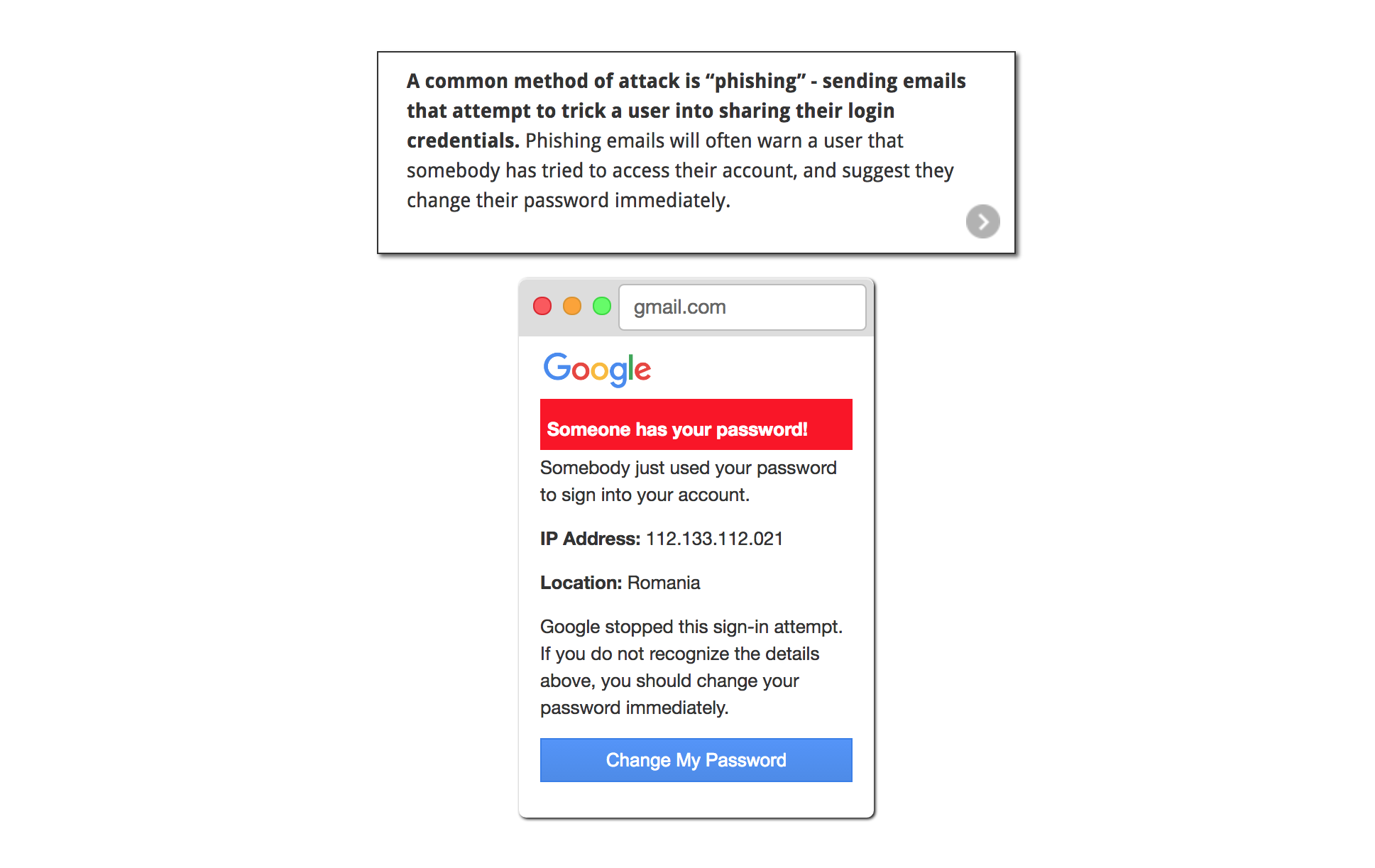
What Is The Best Defense Against Email Spoofing The Daily Vpn Mitigating the risk posed by email spoofing requires a multi layered approach to security. security awareness training can help users to more easily spot and avoid email spoofing attempts. email filters that use dns authentication services like spf, dkim and dmarc can help to lock potentially fraudulent email. Mitigating the risk posed by email spoofing requires a multi layered approach to security. security awareness training can help users to more easily spot and avoid email spoofing attempts. email filters that use dns authentication services like spf, dkim and dmarc can help to lock potentially fraudulent email.

Best Defense Against Phishing Emails Classical Lounge To defend against spoofing attacks, organizations can implement email authentication protocols (spf, dkim, dmarc), employ multi factor authentication (mfa), and use network monitoring tools to detect and mitigate unusual traffic patterns or suspicious activity. why are spoofing attacks such a threat?. The best defense for dns, ip, and arp spoofing is to use a vpn. a vpn encrypts your traffic and hides your real ip address, making it much more difficult for attackers to spoof your identity. for email spoofing, the best defense is to be vigilant about the emails you open and the links you click on. Here are 12 effective tactics to help protect against such attacks: implement dmarc: domain based message authentication, reporting, and conformance (dmarc) allows organizations to specify how unauthenticated emails should be handled and offers reporting mechanisms to monitor suspicious email activity. How to protect yourself from email spoofing. the best defense against email spoofing includes a combination of software and strong online habits. cybercrime is constantly evolving, and defensive technology doesn't always keep up. here, we'll review what you can implement today to lower your risk of falling for a fake message. anti malware.
Personal Data Protection What Are Spoofing Attacks Le Vpn Here are 12 effective tactics to help protect against such attacks: implement dmarc: domain based message authentication, reporting, and conformance (dmarc) allows organizations to specify how unauthenticated emails should be handled and offers reporting mechanisms to monitor suspicious email activity. How to protect yourself from email spoofing. the best defense against email spoofing includes a combination of software and strong online habits. cybercrime is constantly evolving, and defensive technology doesn't always keep up. here, we'll review what you can implement today to lower your risk of falling for a fake message. anti malware. Email spoofing prevention is an integral part of the cybersecurity landscape, aiming to protect end users from being tricked into sharing sensitive data or downloading malware. while robust spam filters, spf, dkim, dmarc represent methods to technically prevent email spoofing, education and awareness are equally important. Spoofing attacks can lead to bad things like name theft, loss of money, and privacy breaches. they can also be used to spread viruses, phishing scams, and other bad software. spoofing can be done in many ways, from easy email tricks to more complex attacks that change ip addresses, arp settings, and dns records. In this guide, we'll explore key strategies to prevent email spoofing, including the use of authentication protocols like spf, dkim, and dmarc, employee training, and email filtering solutions. equip your team with the knowledge and tools to recognize and combat spoofing attempts, and stay ahead of these deceptive cyberattacks. The best practice is an in depth defense approach to detect email spoofing. attackers can change their methods against an organization over time, so an administrator must monitor any changes and check the appropriate warnings and enforcement.

Email Spoofing Defense 101 Email Security Ebook Hashed Out By The Email spoofing prevention is an integral part of the cybersecurity landscape, aiming to protect end users from being tricked into sharing sensitive data or downloading malware. while robust spam filters, spf, dkim, dmarc represent methods to technically prevent email spoofing, education and awareness are equally important. Spoofing attacks can lead to bad things like name theft, loss of money, and privacy breaches. they can also be used to spread viruses, phishing scams, and other bad software. spoofing can be done in many ways, from easy email tricks to more complex attacks that change ip addresses, arp settings, and dns records. In this guide, we'll explore key strategies to prevent email spoofing, including the use of authentication protocols like spf, dkim, and dmarc, employee training, and email filtering solutions. equip your team with the knowledge and tools to recognize and combat spoofing attempts, and stay ahead of these deceptive cyberattacks. The best practice is an in depth defense approach to detect email spoofing. attackers can change their methods against an organization over time, so an administrator must monitor any changes and check the appropriate warnings and enforcement.
