Why Image Based Phishing Emails Are Difficult To Detect Techtarget
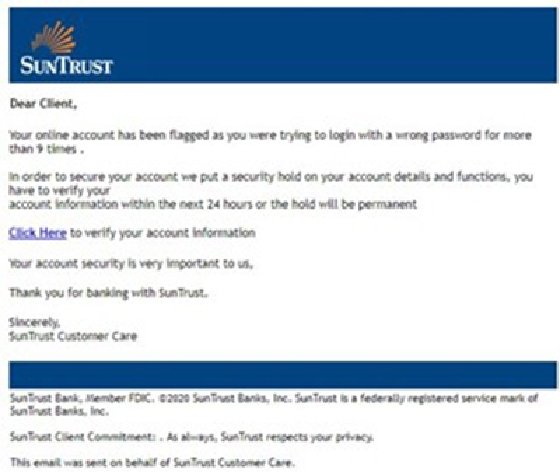
Why Image Based Phishing Emails Are Difficult To Detect Techtarget Phishing mongers have released a torrent of image based junk emails that embed qr codes into their bodies to successfully bypass security protections and provide a level of customization to. Image spam has traditionally been a popular method to circumvent email filters due to the fact there is no textual content for them to analyze. instead the textual content is in the image.

Why Image Based Phishing Emails Are Difficult To Detect Techtarget Attackers are increasingly using images in phishing to evade text based security filters, according to researchers at inky. “secure email gateways (segs) and similar security systems are designed to detect basic textual clues that signal phishing,” the researchers write. Image based fraud in email can be challenging to detect and prevent. by leveraging ai, security teams can make inboxes more secure. Security researchers at inky recently discovered a rash of fraudulent emails that bypass certain conventional spam filters by using image attachments and qr codes. the scams don't appear to. Our results demonstrate that the features of phishing emails and their similarity to the ham emails are reliable predictors of the human detection accuracy of a phishing email.

Problems With Image Based Phishing Emails Safe Yourself Security researchers at inky recently discovered a rash of fraudulent emails that bypass certain conventional spam filters by using image attachments and qr codes. the scams don't appear to. Our results demonstrate that the features of phishing emails and their similarity to the ham emails are reliable predictors of the human detection accuracy of a phishing email. This research investigates the email features that make a phishing email difficult to detect by humans. we use an existing data set of phishing and ham emails and expand that data set by collecting annotations of the features that make the emails phishing. Image based phishing emails are becoming more common because they are more difficult to detect than traditional text based emails. most email filters are designed to scan for text based content, so they can miss image based phishing emails. When incorporated into your secure email gateway, ai based image analysis adds an important layer of protection to your overall cybersecurity strategy. in this post, we’ll examine some of the use cases where the technology can be particularly valuable.

Problems With Image Based Phishing Emails Safe Yourself This research investigates the email features that make a phishing email difficult to detect by humans. we use an existing data set of phishing and ham emails and expand that data set by collecting annotations of the features that make the emails phishing. Image based phishing emails are becoming more common because they are more difficult to detect than traditional text based emails. most email filters are designed to scan for text based content, so they can miss image based phishing emails. When incorporated into your secure email gateway, ai based image analysis adds an important layer of protection to your overall cybersecurity strategy. in this post, we’ll examine some of the use cases where the technology can be particularly valuable.

Problems With Image Based Phishing Emails Safe Yourself When incorporated into your secure email gateway, ai based image analysis adds an important layer of protection to your overall cybersecurity strategy. in this post, we’ll examine some of the use cases where the technology can be particularly valuable.
Comments are closed.